For every system, the firewall is a must have for security. In Linux systems, a firewall can be implemented using iptables command line utility. It is very powerful for setting firewall rules for enhanced security. Under the hood, iptables interact with packet filtering hooks of the kernel’s networking stack known as Netfilter (http://www.netfilter.org/) framework. It can manage packet filtering and NAT rules.
Note: In practice iptables handles IPv4 rules and ip6tables http://linux.die.net/man/8/ip6tables handles IPv6 rules.
Getting Started With iptables
iptables utility uses table concept to organize the firewall rules. Tables, in turn, contains a set of chains. And chains contain a set of rules.
There are four types of tables.
1. Filter table
2. NAT table
3. Mangle table
4. Raw table
5. Security table
Filter table
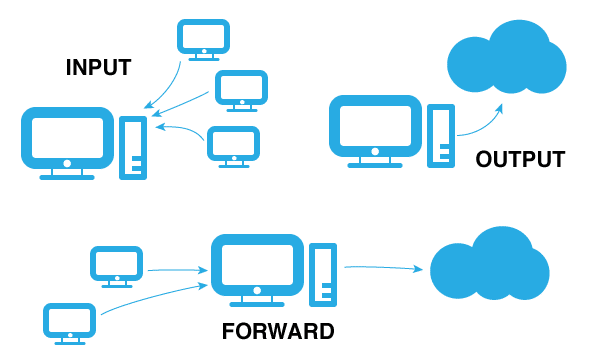
It is the default iptable. This table decides if a packet should be allowed to its destination or not. A typical packet which reached filter table will go through any one of the following three chains.
1. Input chain – If a packets destination to your server, it goes through INPUT chain.
2. Output – If the packets source is your server, then it goes through Output chain.
3. Forward – If the packets, neither the source nor the destination belongs to your server, then it goes through the forward chain. It means the packet from another NIC of your server is being routed. This normally happens when your Linux system acts as a router.
You can view the filter table in your system using the following command.
sudo iptables -t filter --list
NAT table
NAT table contains the following chains.
1. PREROUTING chain – This chain is mainly for DNAT (Destination NAT)
2. POSTROUTING chain – This chain is mainly for SNAT (Source NAT)
Note: Read about DNAT and SNAT with the example from here .
3. OUTPUT chain – If the packets get delivered locally, this chain is used.
You can view the NAT table using the following command.
sudo iptables -t filter --list
Mangle table
This table is primarily used for altering the IP headers. It has the following chains.
1. PREROUTING
2. OUTPUT
3. FORWARD
4. INPUT
5. POSTROUTING
View the mangle table list using the following command.
sudo iptables -t mangle --list
Raw table
This table provides a mechanism to mark packets for opting out of connection tracking. http://people.netfilter.org/pablo/docs/login.pdf
Mangle table has the following chains
1. PREROUTING
2. OUTPUT chain
View the raw table list using the following command.
sudo iptables -t raw --list
Security table
This table is related SELINUX. It sets SELINUX context on packets. To be more specific, it is used for Mandatory Access Control https://en.wikipedia.org/wiki/Mandatory_access_control
View the security table list using the following command.
sudo iptables -t security --list