In this blog, we will look at the components of the AWS certificate manager and how this helps to minimize the creation and management of SSL/TLS certificates.
First, let's start with a brief introduction to AWS Certificate Manager.
To demonstrate AWS certificate manager SSL setup we will do the following.
- Create Certificated on ACM
- Validate Domain ownership
- Setup a apache webserver
- Deploy a Loadbalancer with the ACM certificate and attach the webserver to the loadblancer.
- Map Domain name with Application Load Balancer CNAME
- Validate Domain TLS.
Prerequisites
To follow this blog you should have the following.
- A valid AWS account with admin permissions
- A valid domain name hosted on AWS Route53 or other domain name providers.
What is AWS Certificate Manager?
AWS Certificate Manager where users can request for public SSL/TLS certificates and manage them easily. You can also import third-party certificates to ACM.
These certificates can be used only with AWS internal resources, such as load balancer, CloudFront, Cognito, Bean Stack, API Gateway, etc. You cannot install the certificates created by ACM on any application or web server.
It is a region-based service so you cannot use the ACM certificates created in a region with resources in other regions except for Cloudfront.
To use the certificate in a different region, you need to import the certificate to that region.
Note: Public SSL/TLS certificates requested through ACM are completely free. However, if you want to use Private CA, you can check the pricing from here.
Setup SSL/TLS with AWS Certificate Manager
Here is a simple example of how to generate an SSL/TLS certificate and attach it to an Application Load Balancer.
Step 1: Request ACM Public Certificates
Navigate to the ACM console in the AWS Management Console.
Select the Request option.
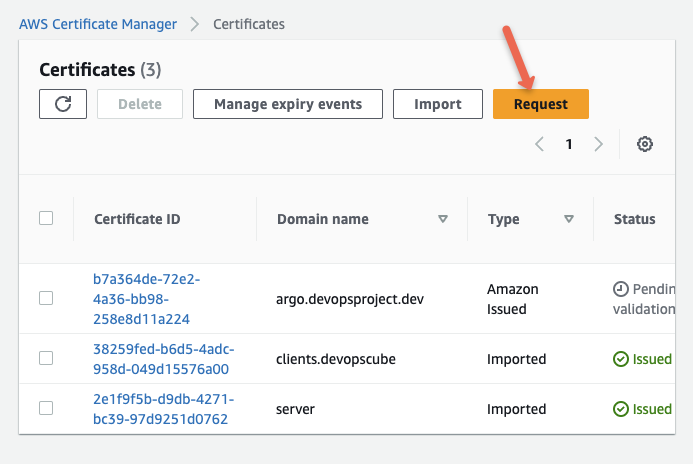
Choose Request a Public Certificate and click next.
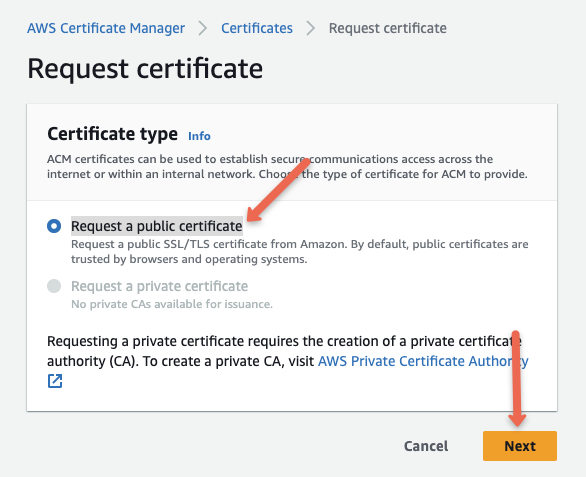
Provide a fully qualified domain name to prove the identity of the website.
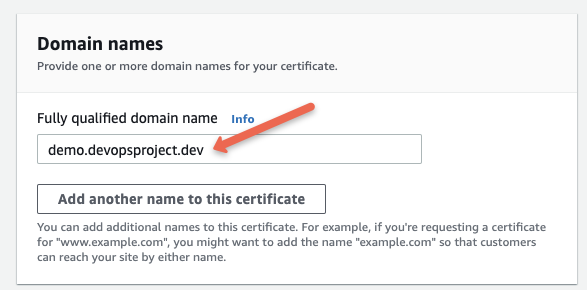
Next choose a validation method
DNS and Email-based validation are available. In DNS validation, DNS records will be generated. For this demo, we are choosing DNS validation.
Next, choose the appropriate key algorithm
RSA and EDCSA are the two supported encryption algorithms available to generate certificates. I will choose RSA.
Next, add the required tags and click request.
Step 2: DNS record validation
Once you request for the certification, you will see a successful notification as shown below.
Click the view certificate option and you will see the pending validation for DNS as shown below.
You need to update the CNAME record to the domain name server for domain validation.
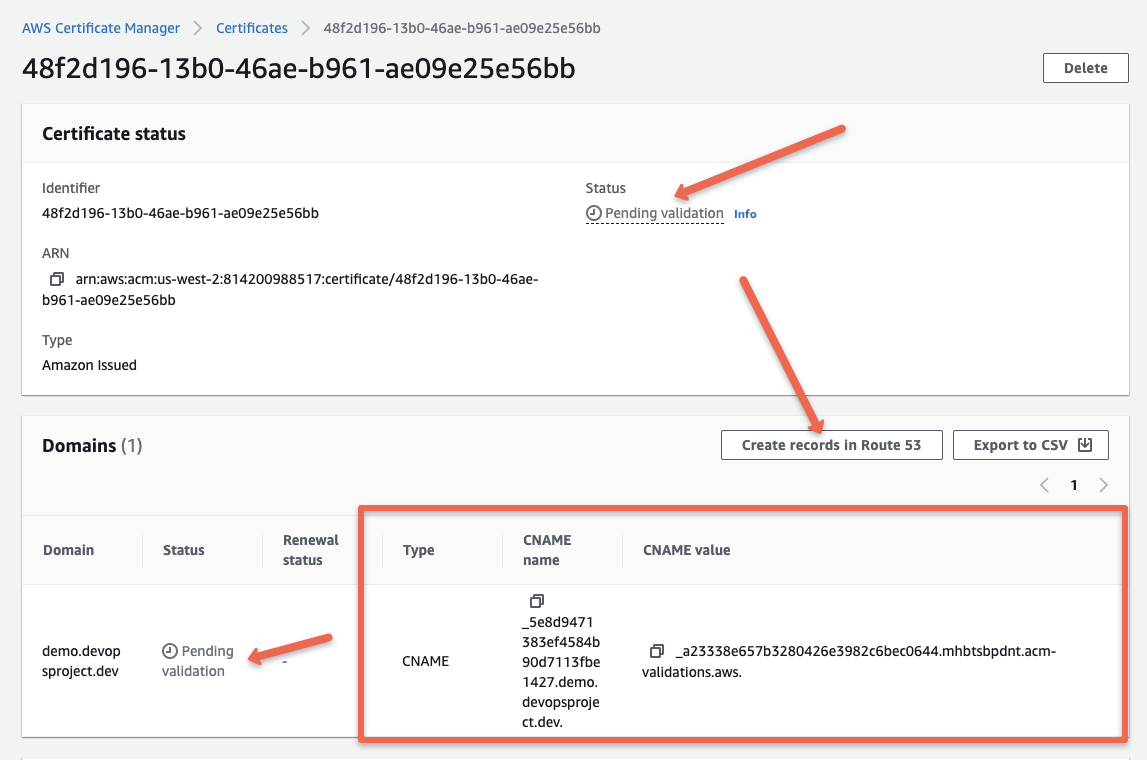
If your DNS is hosted on Route53 you can directly click the Create Records in Route53 option as shown above.
Note: If you are hosting domain name outside AWS, you need to manually add the CNAME record to your DNS settings in the respective DNS provider.
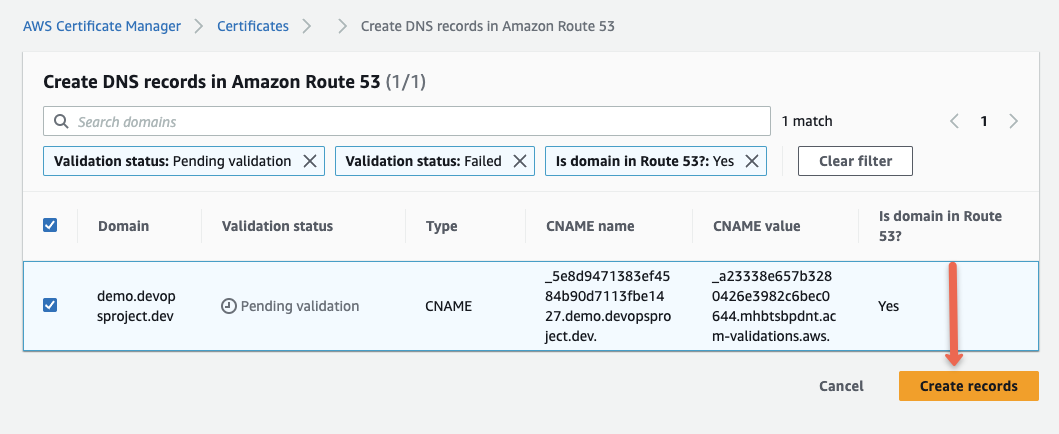
ACM will generate a CNAME DNS record and update it in Route53 automatically. Once created you will see the success message as shown below.
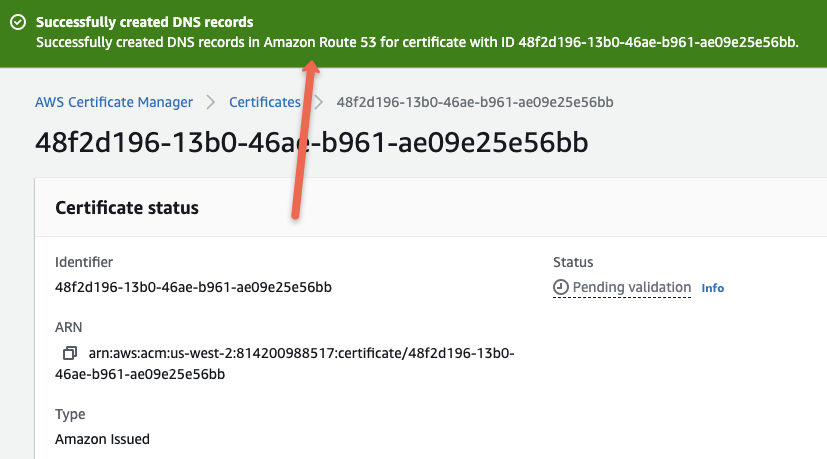
You can also verify this from the route53 dashbaord. You should see the ACM CNAME added to the DNS records.
Step 3: Attach the certificate to the AWS services
Note: Setting up webserver & application load balancer steps are out of scope of this guide. However, you can use the highlevel steps to setup the webserver/application and application load balancer on your own.
For this tutorial demo, I have created an EC2 instance that runs an Apache web server with the default web page.
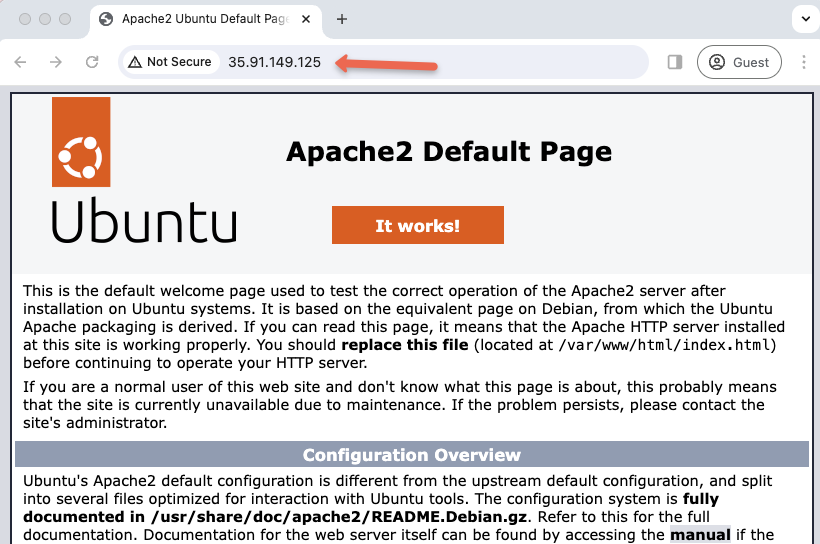
Now we can see the webserver, at present does not have TLS enabled.
To use ACM certificate with the webserver, we have to create a application load blancer and attach to the webserver ec2 instance. Because only with few AWS services you can make use the ACM certificates. You can check the list of supported services from here.
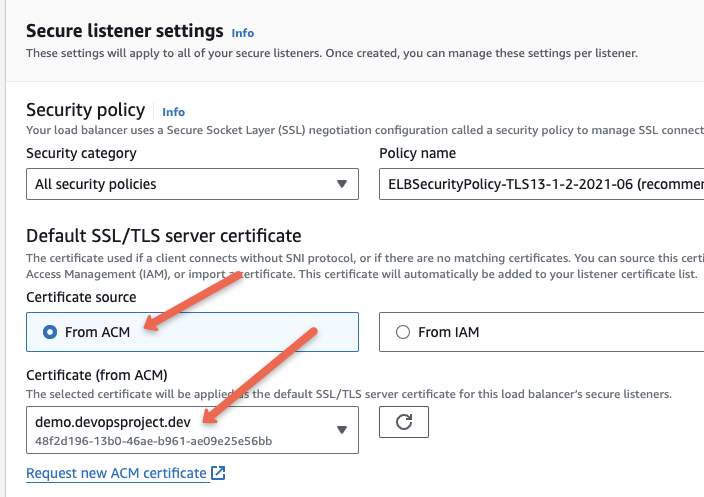
When creating the application load balancer, in the settings you will get the option to add the ACM certificates.
Create an application load balancer for this instance. In the ALB settings under secure listener settings, you will get the option to use the certificate from the ACM as shown below.
Step 4: Map Domain Name to Load Balancer
The next step is to map the domain name to the Load Balancer CNAME.
If you are using Route53, you can use the alias option to map the load balancer CNAME as shown below.
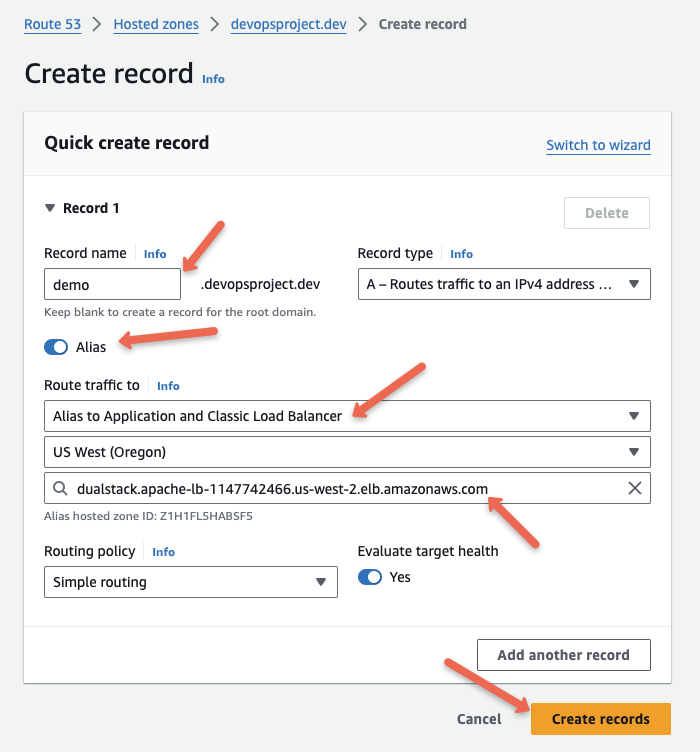
If you are using other DNS providers, you have to create a CNAME entry with the load balancer DNS endpoint.
Step 5: Validate Domain TLS
Once the DNS is mapped with the load balancer, you should be able to access the webserver over DNS with TLS from ACM as shown below.
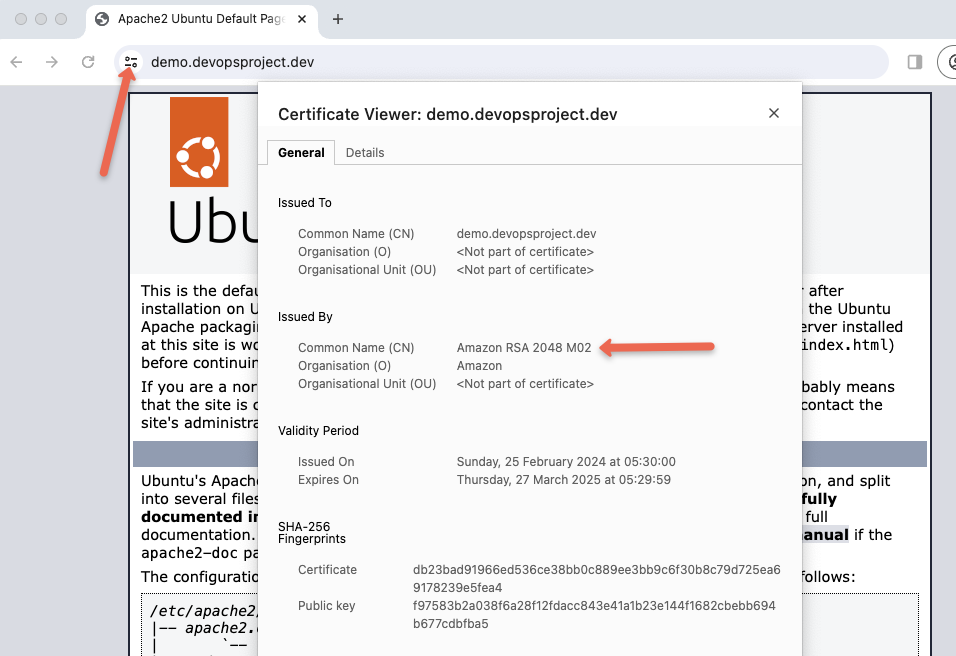
About ACM Certificates
Following are the important information you should know about ACM Certificates.
- AWS Trust Service is a Certificate authority where AWS generates public certificates when we request ACM.
- Most browsers, such as Google Chrome, Explorer, Safari, and Firefox trust certificates that are generated by ACM.
- ACM helps to add additional names for certificates. For example, if the primary certificate name is
devopsproject.dev, we can add another namedemo.devopsproject.devwith this certificate. - ACM follows the X.509 standard to produce the certificates.
- ACM supports RSA and EDCSA algorithms to generate certificates. The key sizes for RSA are 1024, 2048, 3072, and 4096. The key sizes for EDCSA are 256, 384, and 521.
- ACM Certificates are valid for 13 months (395 days).
- ACM renews certificates automatically if you use DNS validation and CNAME record remains in place.
- For manual renewal , ACM will notify us 45 days before the expiration. For renewal, ACM verifies the domain ownership using DNS records and also ensures the certificates are currently in use. For email-validated certificates, a notification will be sent to the email, the owner can renew the certificate by clicking the link.
To generate an SSL/TLS certificate, a pair of keys is required (public and private). The public key is a part of the certificate.
ACM will generate a key pair if you request to Certificates and it will securely store the private key in the AWS Key Management System.
When we integrate this certificate with AWS services, AWS KMS provides the encrypted private key and a grant that AWS KMS created to decrypt the private key.
This is how AWS maintains the security between certificates and services. To learn more about the AWS KMS grant, please visit the official documentation.
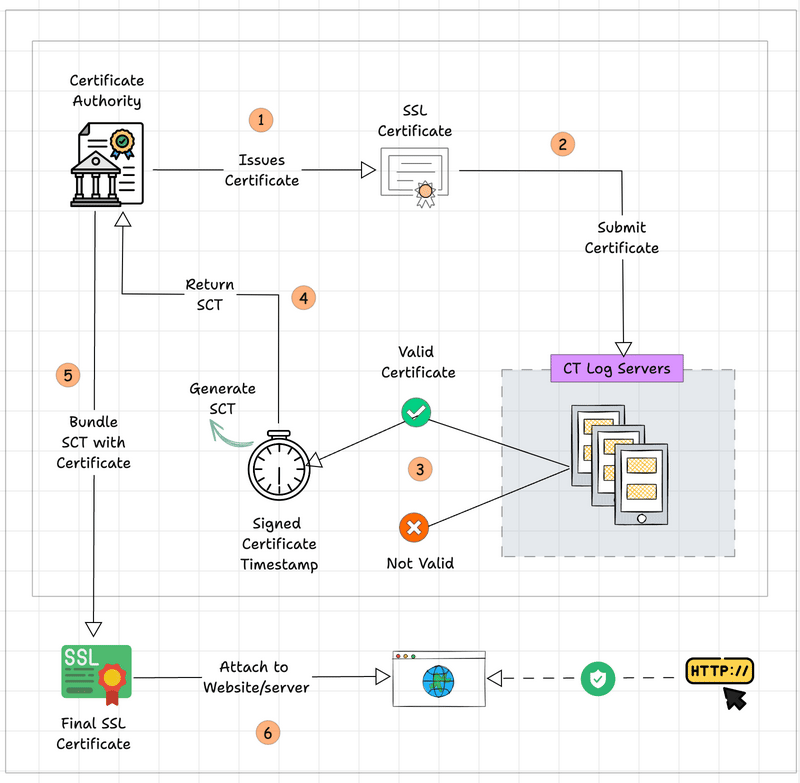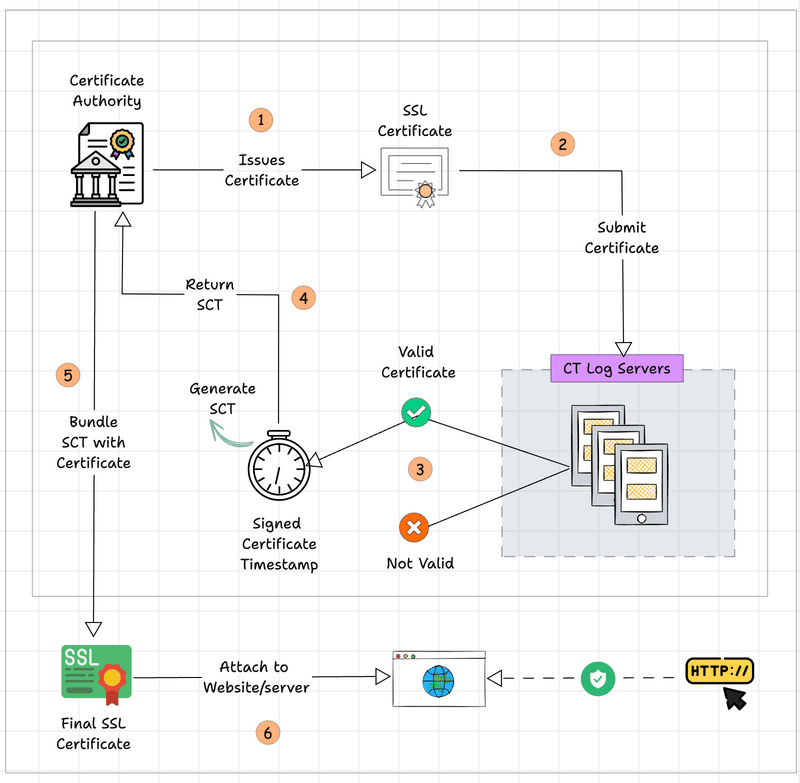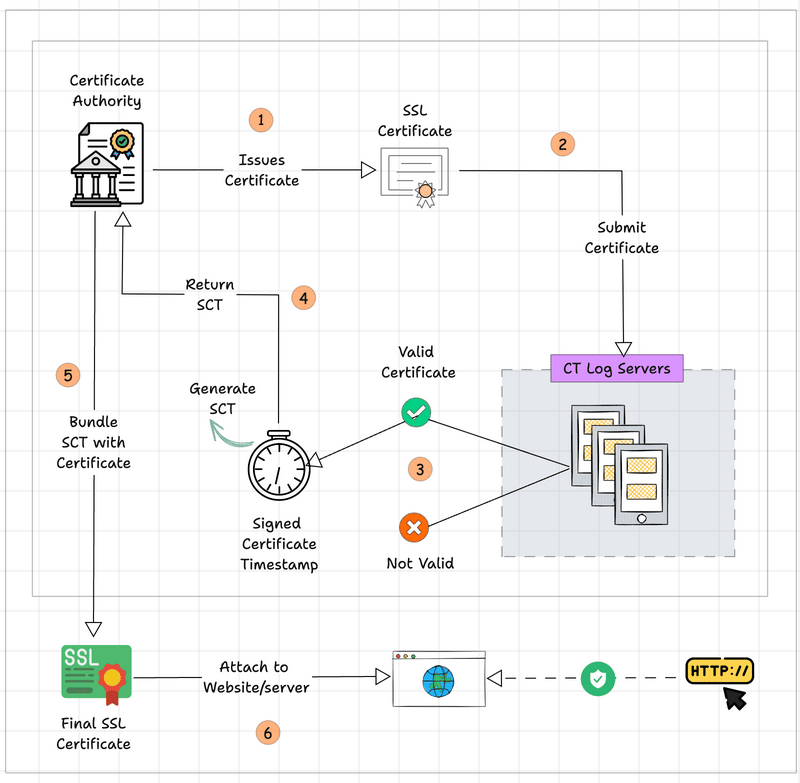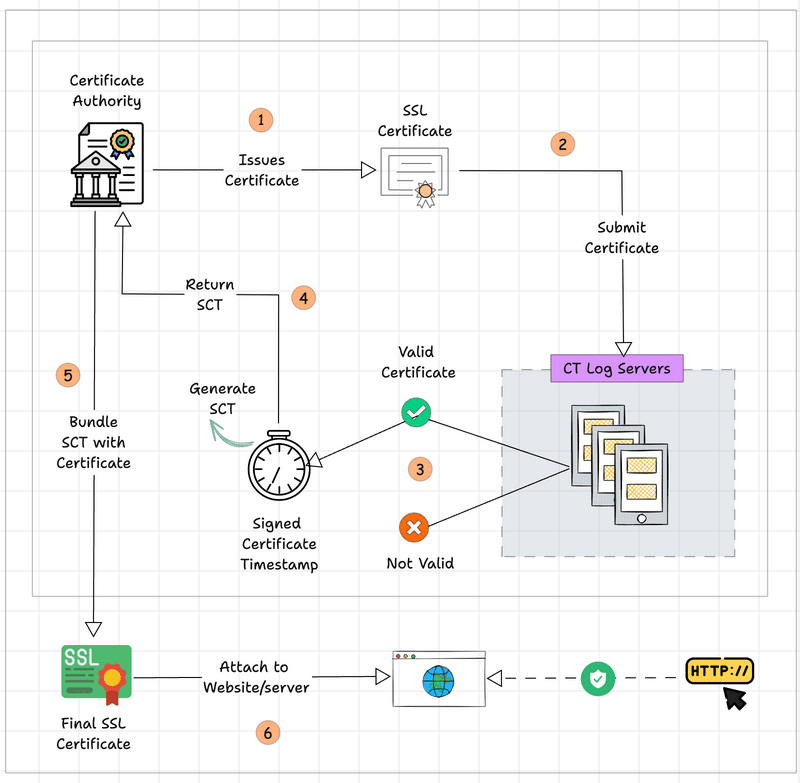
Certificate Transparency Logging
When generating a certificate, the Certificate Authority should provide the report to the log server.
This log is publicly available and helps to ensure the integrity of the certificates. If this one-time process wasn't done by CA, you may see a security warning when you try to access the website.
Enabling Certificate Transparency has been a mandatory function since 2018.
If you are requesting a certificate to ACM, the Certificate Transparency function will be enabled by default, also you can not control this through AWS Console.
But if you are using Terraform or other IAC tools to provision SSL/TLS certificates from ACM, make sure you enable the Certificate Transparency Logging function.
ACM Vs. AWS Private CA
Certificates are generated from AWS Certificate Manager by an AWS public Certificate Authority. We can use this to secure our websites to public access.
While the certificates which are generated by AWS Private Certificate Authority are used to secure our private network communication.
Combining these two types of certificates is also possible. we can create an AWS Private CA and generate certificates to secure internal resources.
Also, we can manage the lifecycle of these certificates from ACM. while we can generate public certificates directly from ACM and attach them with public-facing resources to secure communication.
Conclusion
The default quota to generate ACM certificates and import certificates from outside is 2500 and this is not included with Private CA.
You can also check out out AWS Client VPN blog where we have used ACM to store client and server certificates.
To know more about the quota, please refer to the official documentation.


