In this guide, we will look at AWS load balancers, their types, and the key concepts involved.
What is AWS Elastic Load Balancing?
Elastic Load Balancing is a managed load-balancing service by AWS. It distributes incoming traffic across different resources such as EC2 instances, containers, and IP addresses in one or more Availability Zones.
Elastic Load Balancing service comes under Networking & Content Delivery services.
From a networking standpoint, AWS Load balancers can be set to internal (private) or Internet Facing (Public).
AWS Load Balancer Types
Now let's look at the different load balancer types supported by AWS.
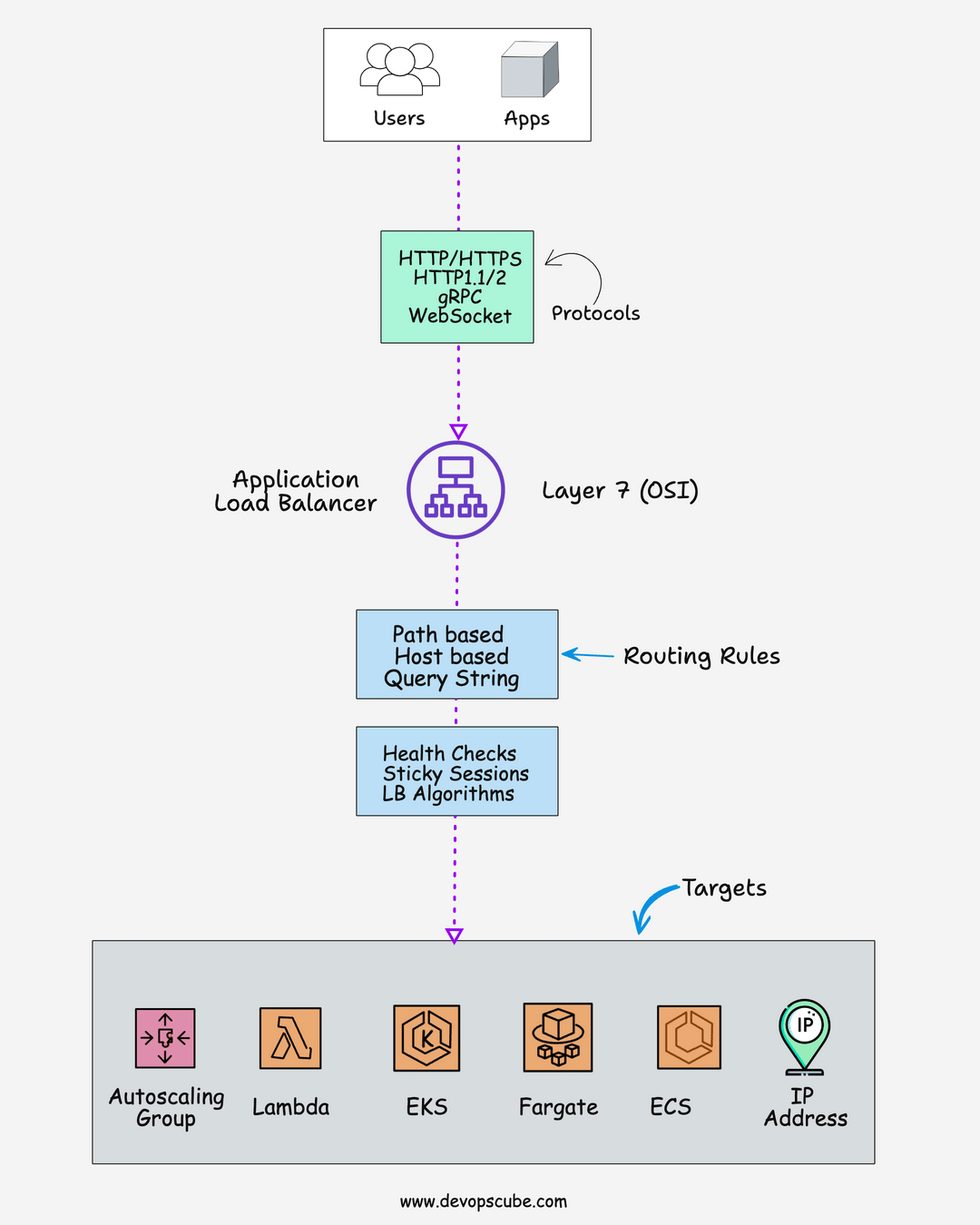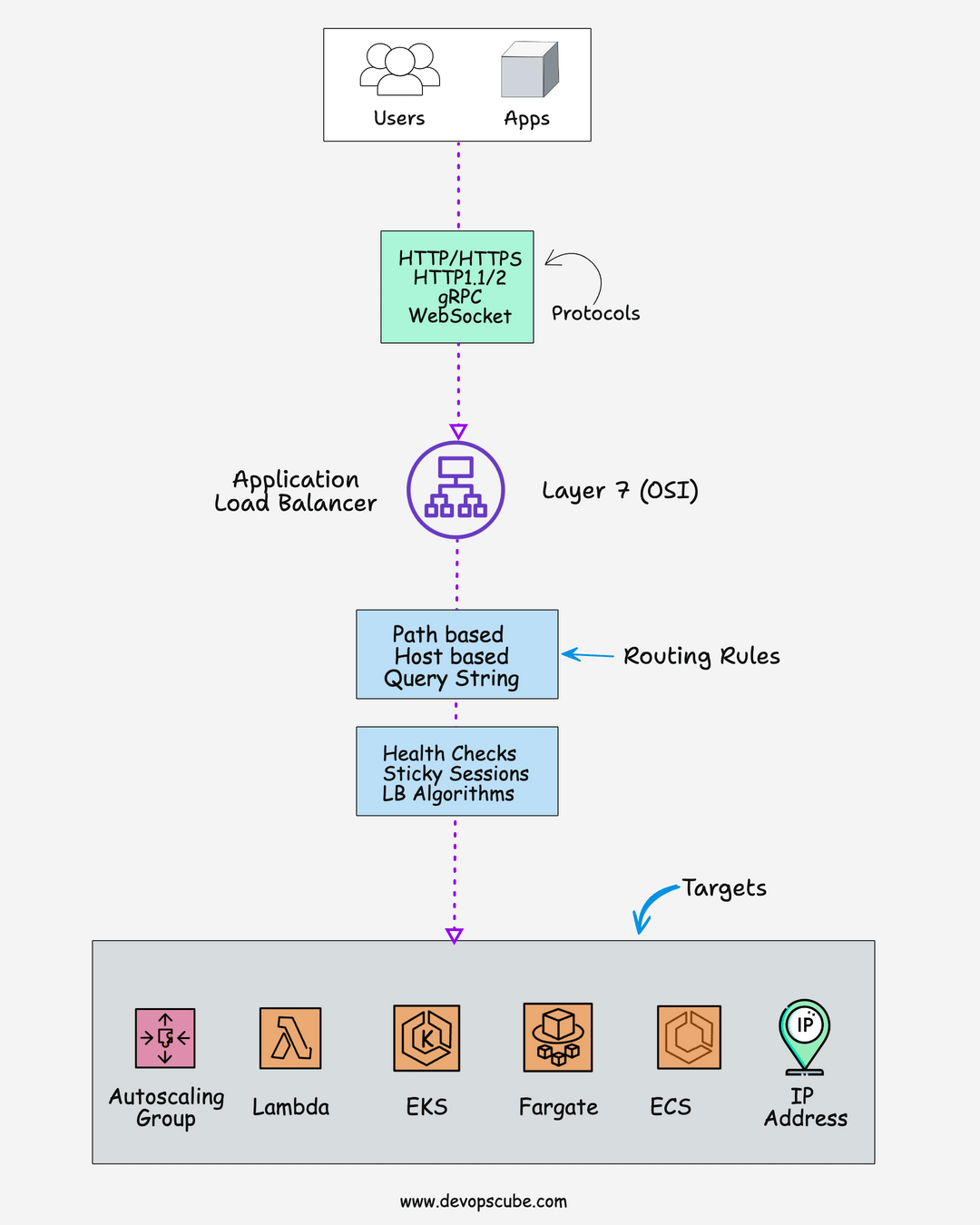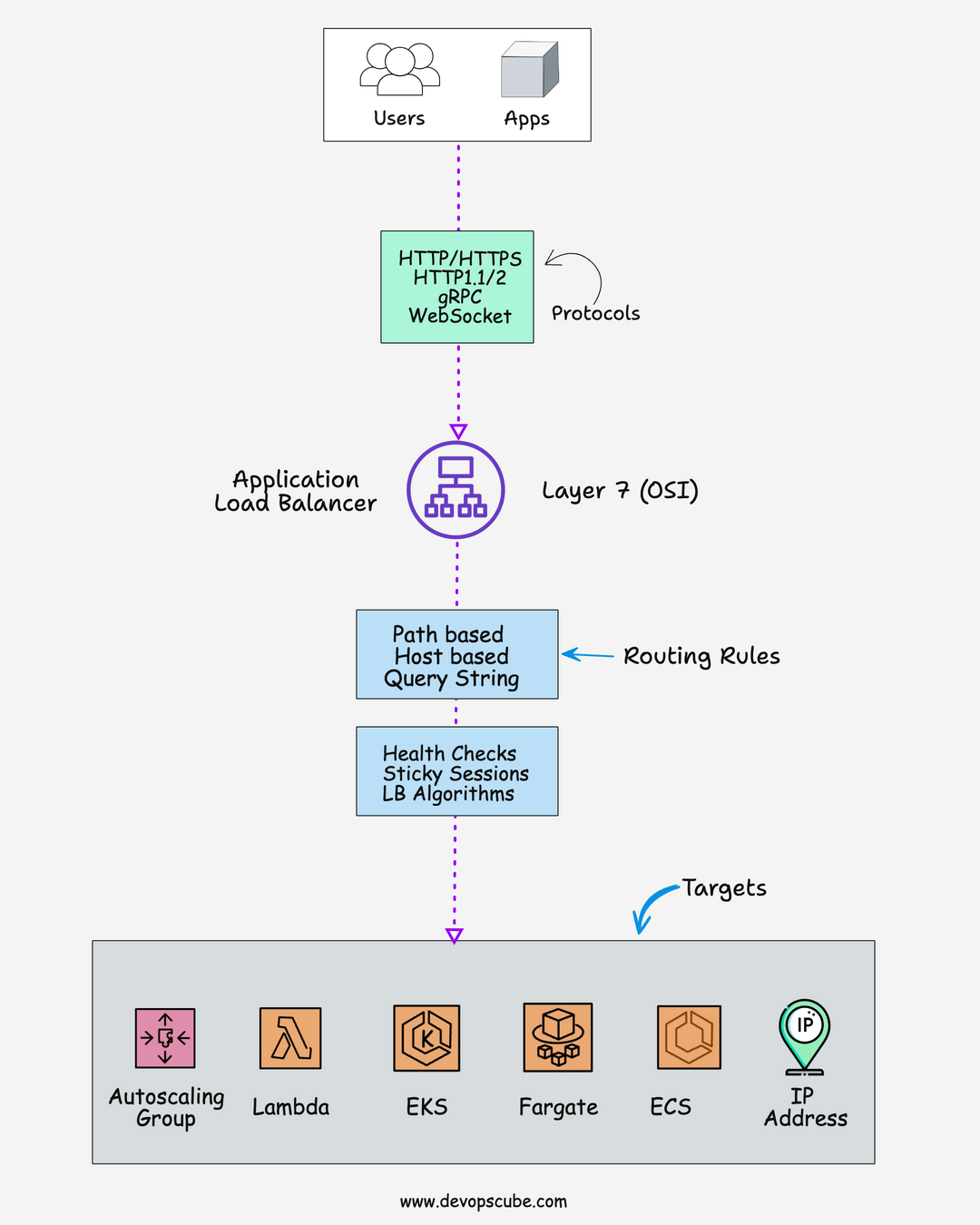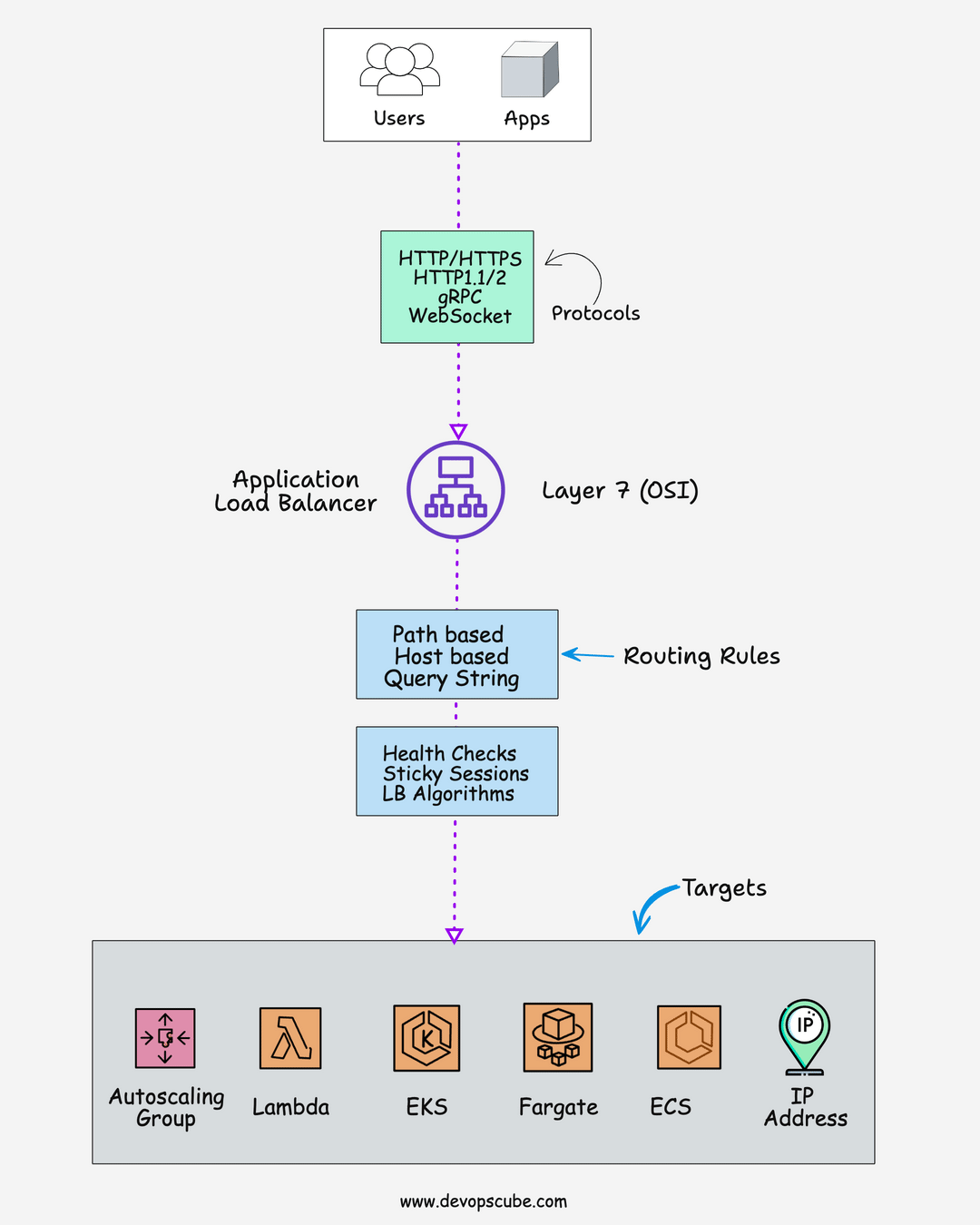
🏋️♂️ Application Load Balancer
Example Use Cases: Web applications, Microservices & API gateways
Here is what you should know about the AWS Application load balancer.
- ALB runs at the application layer, which is OSI layer 7.
- ALB supports routing rules like path-based routing, host-based routing, and query string routing.
- You can add a security group to ALB to allow incoming traffic only on specific ports and sources.
- ALB stickiness features allow requests from a particular client to be consistently routed to the same target.
- Supports protocols like HTTP, HTTPS, HTTP/2, gRPC, WebSockets, etc.
- Supports IPV4 and Dualstack IP address types (IPV4 & IPV6)
- Targets can be Autoscaling Groups, Lambda Functions, Fargate, EKS cluster, ECS, or an IP address.
- ALB does not support Static IP addresses.
- SSL/TLS connection gets terminated at the ALB level. From ALB the backend targets receive decrypted traffic. However, you can have encrypted traffic from ALB to targets by installing TLS certificates on targets. If you have any compliance requirements to pass encrypted traffic to targets, you should consider NLB.
- Supports 25 TLS certificates per ALB by default but it can be increased. Check ALB quotas for more information
- ALB does not support MTLS.
Note: If you want to prepeare for AWS certifiations, you can try learn.cantrill.io to get access to premium AWS certification content.
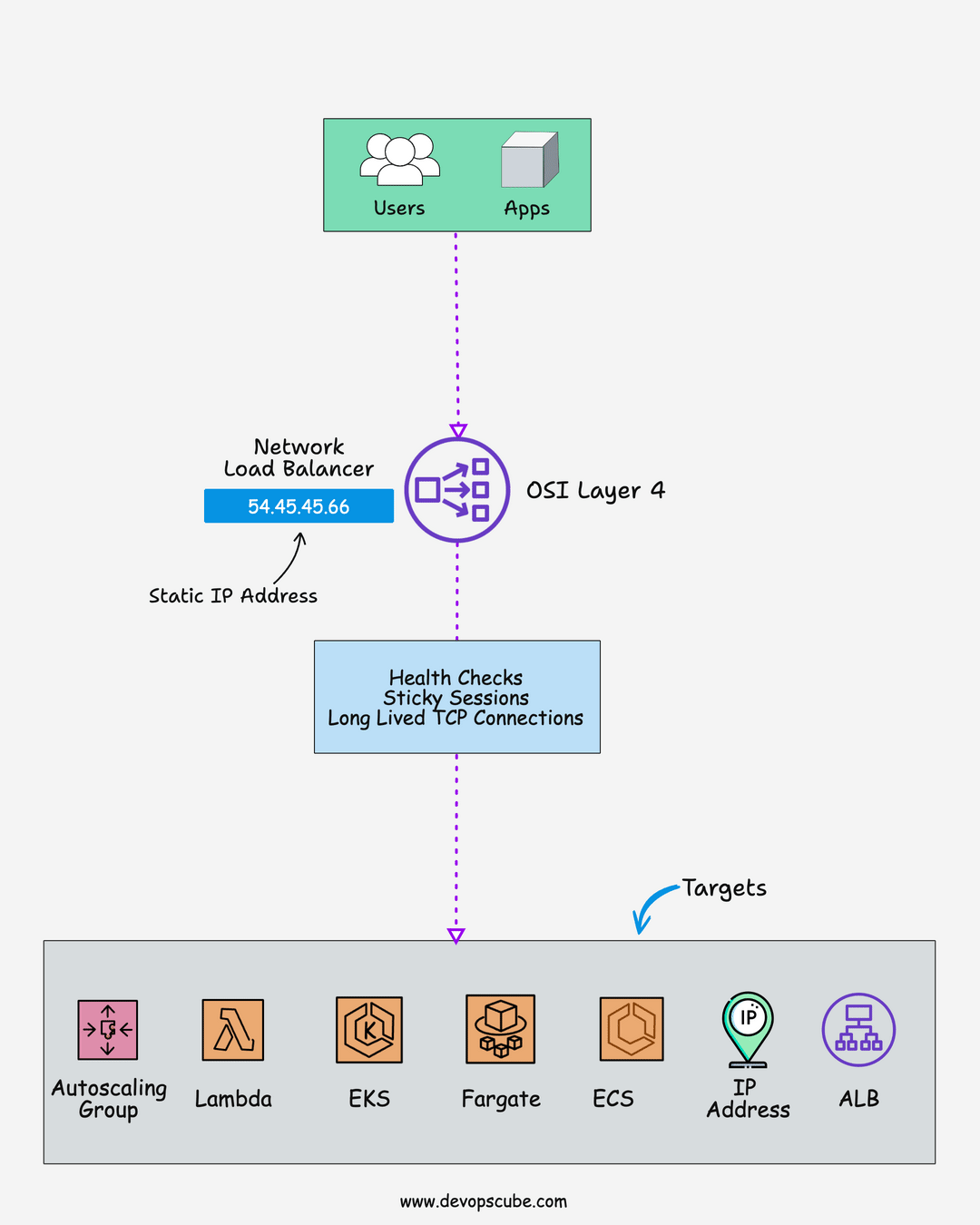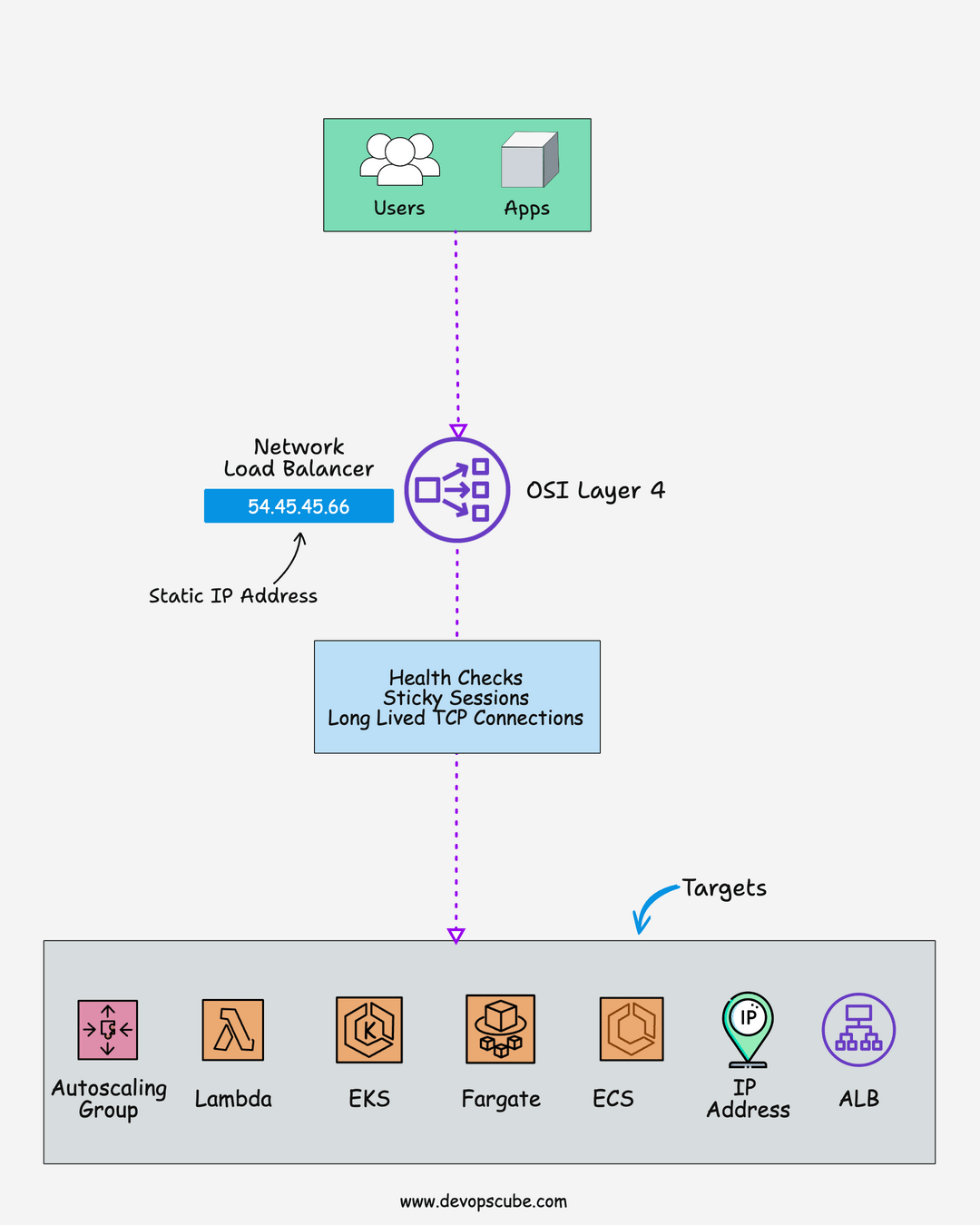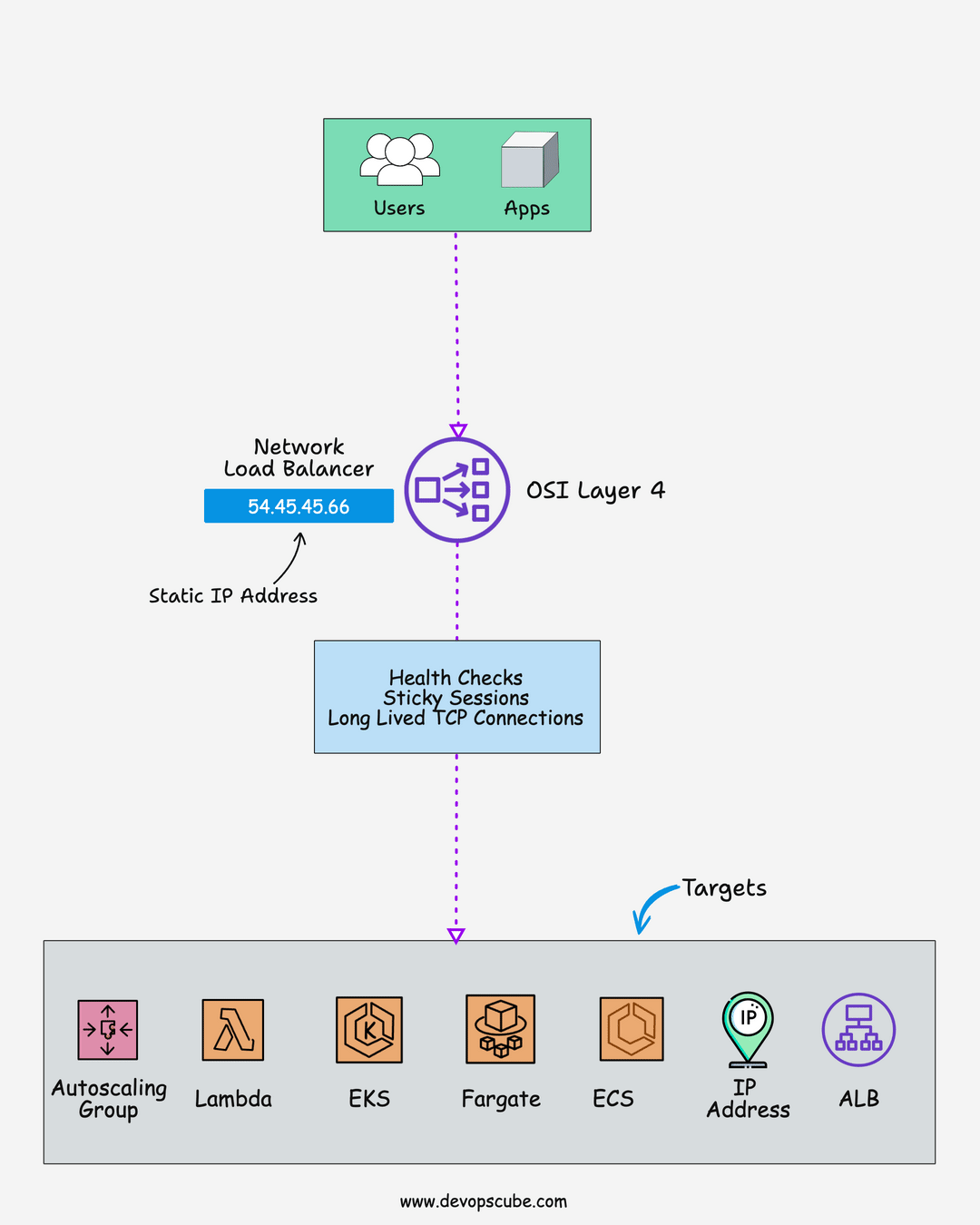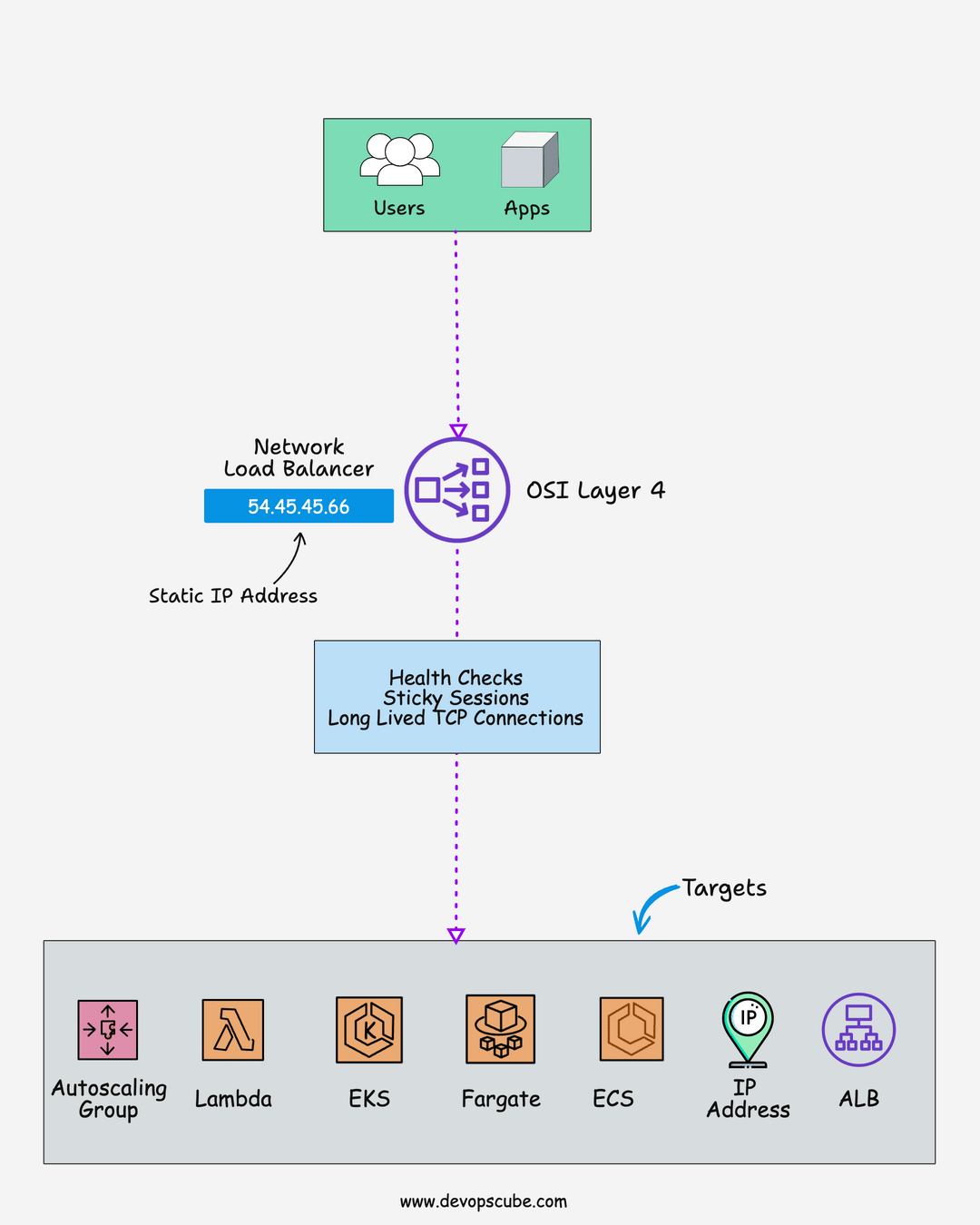
🌐 Network Load Balancer
Example Use Cases: Gaming/VoIP/streaming media servers, financial trading applications
Here is what you should know about the AWS network load balancer.
- The network load balancer is an ideal choice for high-performance applications. It is built for handling volatile traffic patterns and millions of requests per second.
- Support protocols like TCP and UDP
- Support static IP address.
- You can add security groups to NLB. This feature was added recently.
- NLB runs at the transport layer which is OSI layer 4
- With NLB, you can route requests to multiple applications running on a single ec2 instance on different ports.
- NLB supports TLS-encrypted traffic till the targets.
- NLB can handle more traffic than ALB.
- Supports 25 TLS certificates per NLB by default but it can be increased. Check NLB quotas for more information
🛡️ Gateway Load Balancer
Real-World Use Cases: Firewall Management, intrusion detection, and prevention systems.
Here is what you should know about the AWS Gateway load balancer.
- The gateway load balancer is used for creating, scaling, and managing virtual services like intrusion detection in the AWS cloud.
- GLB runs at the network layer, that is OSI layer 3.
- It can load balancer traffic across multiple virtual appliances (Firewalls, WAFs, CDNs, etc)
- It can act as a single entry and exit point for all traffic.
- Forwards traffic using GENEVE protocol on port 6081
While AWS offers the Network Firewall service, many organizations utilize their on-premise firewall systems on AWS. Here is where GLB plays a key role.
If you want to understand more about how gateway load balancers are used in the real world, I would suggest the following blogs of well know virtual appliance providers.
🕰️ Classic Load Balancers
Classic load balancers are older load balancers that are no longer used for new deployments.
AWS Load-Balancing Algorithms
For distributing traffic to multiple resources, AWS load balancers support different types of Load balancing algorithms. Some of the most used algorithms are given below:
- Round Robin (default ALB algorithm)
- Least outstanding requests (LOR) - Supported on ALB
- Flow hash algorithm (Used by Network Load Balancer)
You can modify the algorithm parameter in the target group attributes.
AWS Load Balancer Key Concepts
Some Important concepts of load balancer are listed below.
Target Groups
The primary work of a load balancer is to route traffic to backend instances or targets.
A Target group is a logical grouping of targets such as ec2 instances, Lambda functions, EKS cluster, IP address, etc.
Listeners
The listener is a configuration where you specify the port and protocol for the front end of the load balancer and the protocol and port for the backends
Meaning, the client has to interact with the load balancer on that specific port and protocol.
It also forwards the incoming client requests to the configured backend target groups
Health Checks
The health check is the mechanism for the Load balancer to check the status of the backend targets and route only traffic to healthy targets.
Here is what you should know about health checks.
- Monitor the health of registered targets using the health check intervals (default is 30 seconds)
- Health check support HTTP, HTTPS, and TCP protocols.
- NLB uses active and passive health checks
- Health checks are part of target group configurations.
ALB Vs NLB Vs GLB
The following table shows the differences between AWS ALB vs NLB vs GLB
| Feature | ALB | NLB | GLB |
|---|---|---|---|
| OSI Layer | 7 | 4 | 3 |
| Routing | Content-based | IP address and port | Source and destination IP addresses and ports |
| Protocols | HTTP, HTTPS, TCP, UDP | TCP, UDP, TLS | TCP, UDP, TLS |
| Use cases | Applications that need to perform advanced routing | Applications that need to handle high volumes of traffic with low latency | Applications that need to provide connectivity to virtual appliances |
| Supported Algorithms | Round Robin Least outstanding requests | Flow hash algorithm | GENEVE protocol |
Load Balancer Monitoring
AWS provides native ways to monitor the Load balancer.
You have the following options for monitoring a Load balancer
- Cloud Watch Metrics: To collect load balancer metrics
- Access logs - Detailed logs of all requests that are made to your load balancers
- Request tracing: To track HTTP requests through your load balancer and backend targets. The load balancer adds X-Amzn-Trace-Id header to every request it receives from the client.
- CloudTrail logs: To track all the API calls made to the Elastic Load Balancing API.
AWS Load Balancer Controller
AWS Load Balancer Controller is a Kubernetes controller responsible for managing Load Balancers for AWS EKS clusters.
The requirement for a Load balancer is for exposing Kubernetes Service and for ingress.
- You can create a Kuberntes service type LoadBalancer using Network Load Balancer (NLB)
- You can set up an ingress controller using an Application load balancer.
Load Balancer Pricing
Pricing of the load balancer is based on the following factors
- Type of load balancer: The pricing for each type of load balancer is different.
- Hours used: Charged per hour basis.
- Data Transferred: Charges application for data transferred through the Load balancer for public and private traffic. You are not charged for data transfer within AWS services, region, and AWS Outposts environment.
- Region: Pricing differs based on AWS regions.
Here is what you should know about AWS load balancer pricing.
- The application and Network load balancer have a free tier of up to 750 hours.
- Discounts on pricing are applied on sustained usage of load balancers.
- NLB is expensive compared to other load balancer types.
Check the official ELB pricing page to know more. To understand the pricing estimates, use the AWS Pricing Calculator.


