In this blog, we will look at the list of best service mesh tools for microservices that provides security, canary deployment, telemetry, load balancing, and much more.
The number of service mesh tools for deploying and operating microservices is ever-increasing. In this post, we will explore the top service mesh tools that you should be using to build your own service mesh architecture.
The first thing to do when developing a strategy for selecting the right tool is to understand what it will provide you with and how well it works.
What is a Service Mesh?
wikipedia.org
What if you want to manage, monitor, and secure communications between all microservices? Here is where a Service mesh comes into the picture.
A service mesh is a tool that provides an abstraction layer for microservices. They provide intelligent routing, resiliency, and load-balancing capabilities between services with better fault tolerance than traditional solutions.
Overall, a service mesh manages all the service-to-service communication. It intercepts all the traffic flow between services. The best part is, you can manage all the service mesh functionalities in a declarative way, the same manner you deploy objects in Kubernetes.
What does a Service mesh do?
A service mesh essentially manages the traffic flow between multiple microservices primarily using a sidecar proxy.
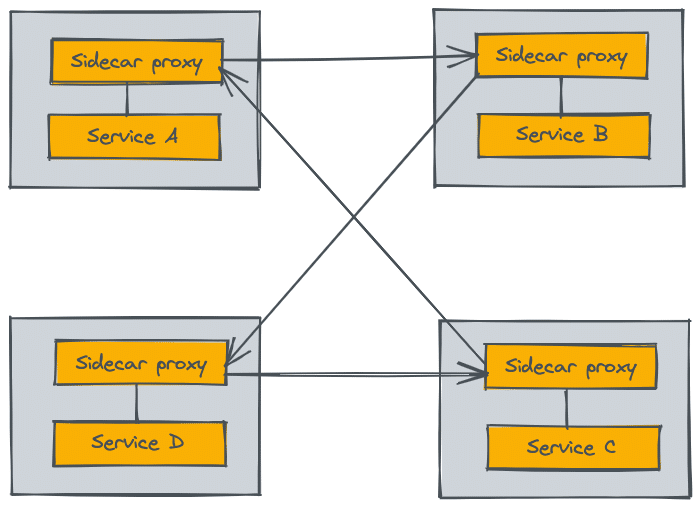
There are many benefits from using a service mesh including increased security by providing communication encryption, simplified debugging processes through observability tools, as well as higher availability due to smart failover features and horizontal scalability with distributed tracing across containers or machines.
A service mesh aims to provide the following features
- Routing & Load Balancing
- Service discovery
- Authentication and authorization
- Canary deployments
- Circuit breaking, Rate limiting, Health checks, and retry budgets
- mutual Transport Level Security (mTLS) & Access control lists.
- Observability through Distributed tracing
- Access logs of service-to-service communication
In most cases, a sidecar container running along with the application container takes care of all the above-mentioned features. You don't have to specially design an application to work with a service mesh. Also, there is no extra instrumentation required to monitor services with service mesh capabilities.
What are the Best Service Mesh Tools?
Here is our pick on top service mesh tools
1. Istio
| Github | Istio Open Source repo |
| Official Website | istio.io |
| Learning | Istio Official Documentation |
Istio is a service mesh that was originally developed by Google but is now open source. Istio provides a way to connect, manage and secure microservices that communicate with each other.
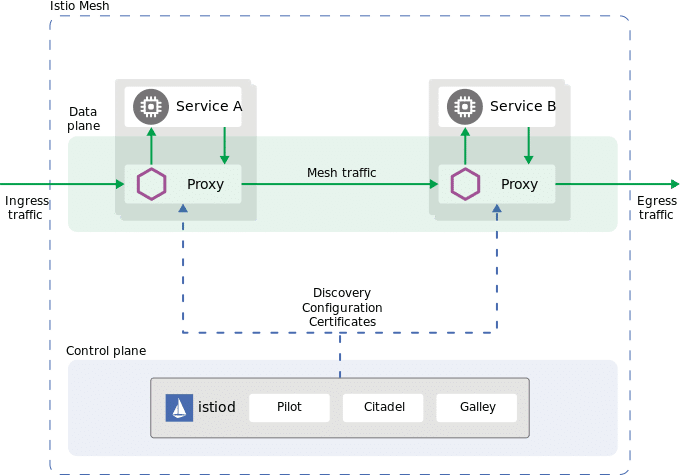
Istio’s security features include encrypting all communication between services in transit as well as providing authentication credentials for authorized users. Istio also offers functionality such as distributed tracing across containers or machines without the need for third-party software agents within individual nodes.
Istio is used in production by many companies such as Adobe, Baidu, and Google.
If you want to get started with Istio, refer our detailed Istio Setup guide.
Here are some Istio production stories.
2. Linkerd
| Github | Open Source repo |
| Official Website | linkerd.io |
| Learning | Official Documentation |
Linkerd is an open-source service mesh that can run on top of Kubernetes or a Mesos cluster and is designed for high-scale environments to manage large numbers of microservices.
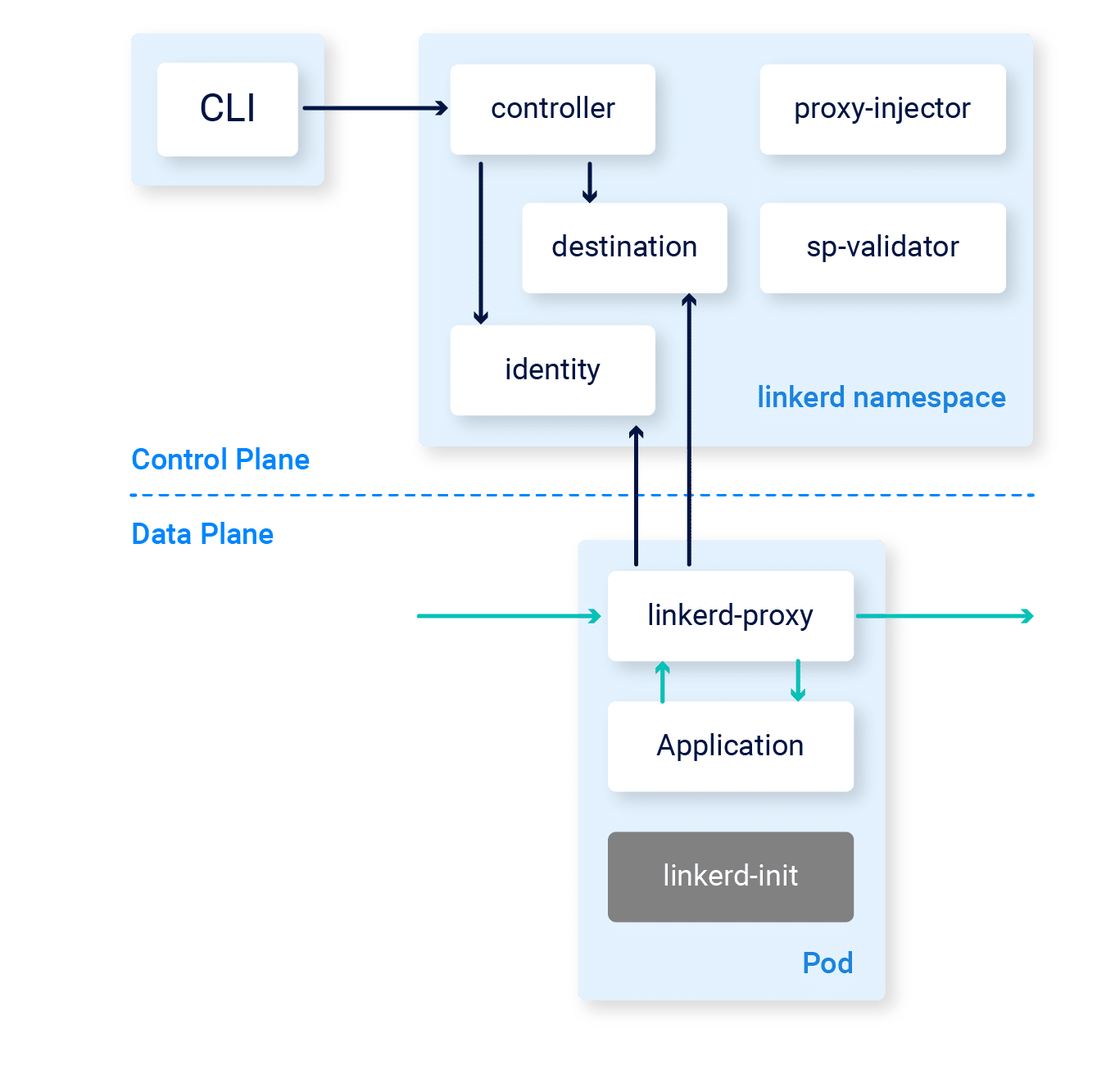
Linkerd will also provide monitoring, tracing, routing, load balancing, and other features as well as automatic deployment upgrades across clusters
Few Linkerd production-related readings,
- Buoyant’s Linkerd Production Runbook, from the creators of Linkerd.
- Linkerd service mesh in production
3. Cilium Service Mesh
| Github | Cilium Open Source repo |
| Official Website | cilium.io |
| Learning | Official Documentation |
Cilium is an open-source, lightweight network and security solution for containers and microservices. It uses the Linux kernel's BPF (Berkeley Packet Filter) technology to provide transparency, visibility, and security for containers and microservices. Cilium provides a flexible way to containerize and microservice-ify applications without being tied to any specific orchestration solution.
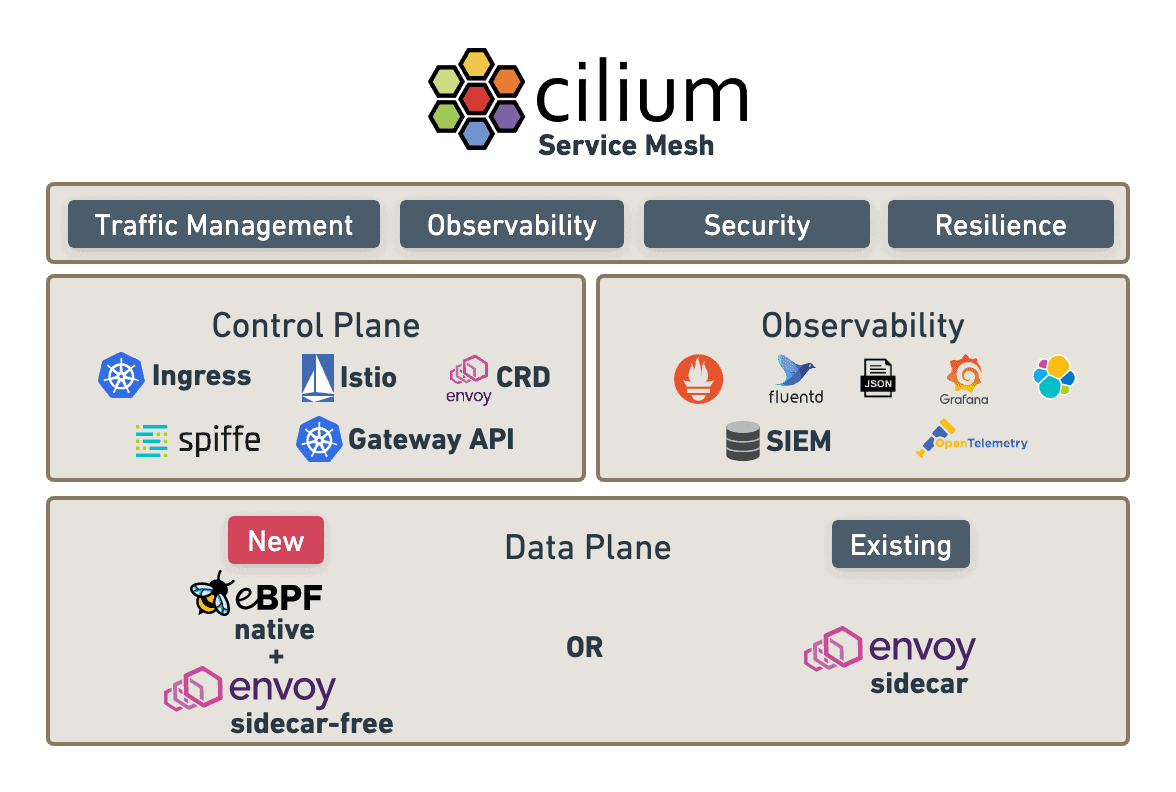
- Container and microservice-aware network policies
- Automatic discovery of services
- L7 (Layer 7) aware policy enforcement
- A Unified security model for containers and hosts
- Fine-grained security visibility
- Secure communications between containers and microservices
- No need for a central controller or management overhead
Cilium is an easy way to improve the security and networking of your containerized applications without changing any code. Cilium integrates with popular orchestration solutions such as Docker, Kubernetes, and Mesos and can be used with any Linux-based application.
If you're looking for a lightweight, easy-to-use solution for securing and networking your containers and microservices, Cilium is the right choice for you.
4. Consul connect
| Github | Open Source repo |
| Official Website | consul.io |
| Learning | Official Documentation |
Consul Connect is a service mesh solution from Hashicorp.
Consul was initially designed for service discovery. However, with the consul connect, the service mesh is deployed on top of the consul and provides service discovery, configuration synchronization, and failure detection.
Consul Connect can run in production with or without Kubernetes.
5. Traefik Mesh
| Github | Open Source repo |
| Official Website | traefik.io |
| Learning | Official Documentation |
Traefik Mesh is a simple service mesh solution, primarily used for load balancing.
Traefik Mesh is a plug-in for the popular reverse proxy Traefik that aids in service discovery and routing between services to balance out workloads.
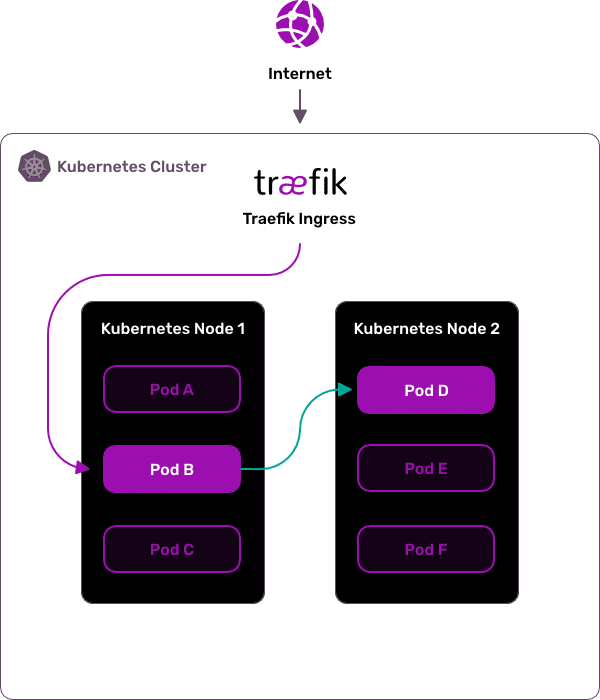
It also provides features like SSL termination and web socket proxying so you don't have to worry about those things on your own if they
6. Open Service Mesh (OSM)
| Github | OSM repo |
| Official Website | openservicemesh.io |
| Learning | OSM Official Documentation |
Open Service Mesh (OSM) is a lightweight and extensible cloud-native service mesh that supports dynamic service discovery, monitoring, and routing.
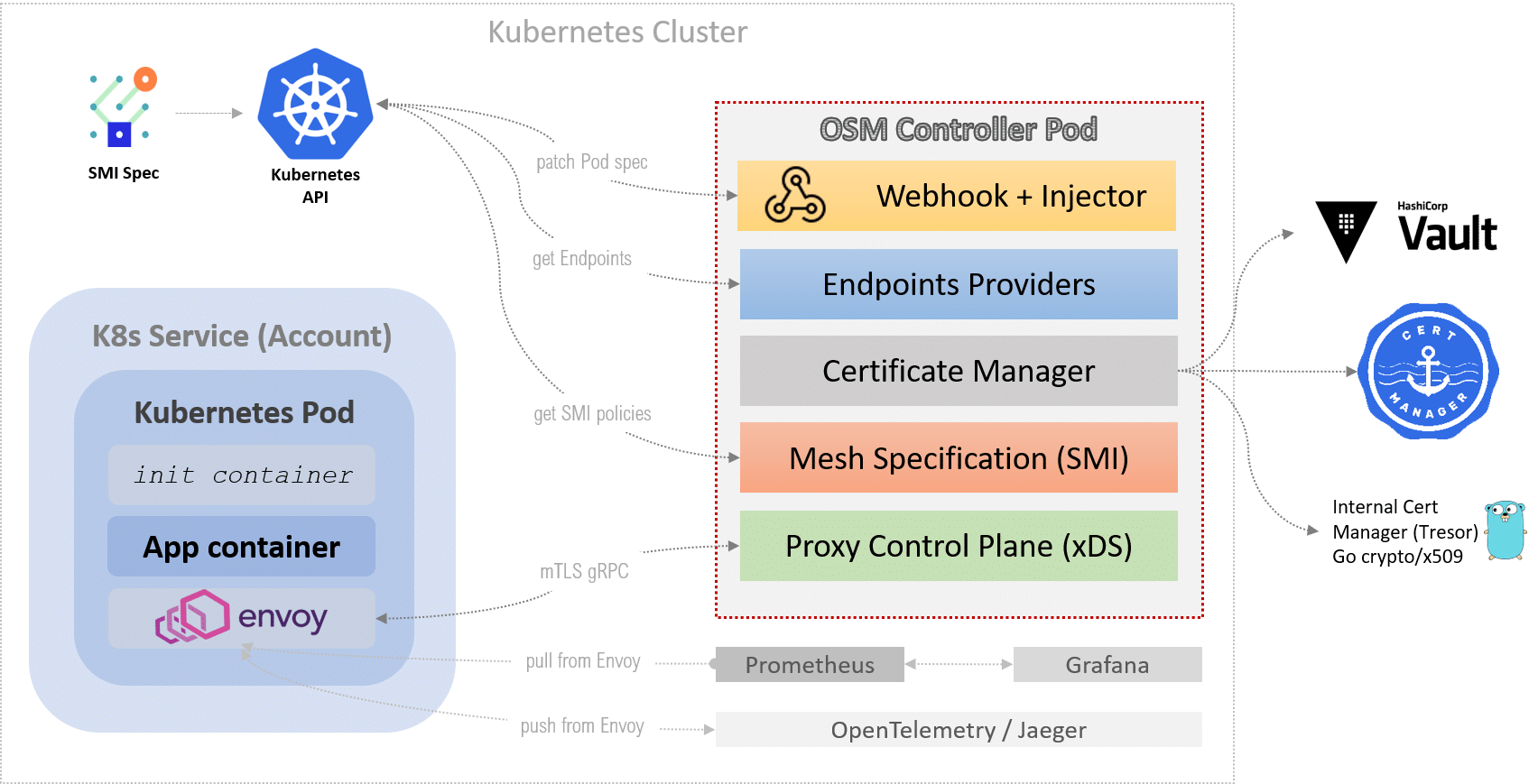
OSM is pluggable at all levels to provide the best fit for your requirements:
- Service Discovery - Layer four (IP), or layer seven (URL)
- Monitoring – Prometheus-based metrics with backends supporting Graphite, InfluxDB, and Elasticsearch
- Routing - HAProxy as a proxy between services providing high availability via load balancing of requests across pods in a cluster. It also provides features like SSL termination and web socket proxying so you don't have to worry about those things on your own if they run over insecure protocols such as plaintext TCP/UDP connection. This helps ensure access control by only allowing traffic from authorized IPs through service mesh.
7. Nginx Service Mesh (NSM)
Nginx service mesh is a lightweight service mesh for kubernetes with a zero-trust environment providing encrypted traffic between containers.
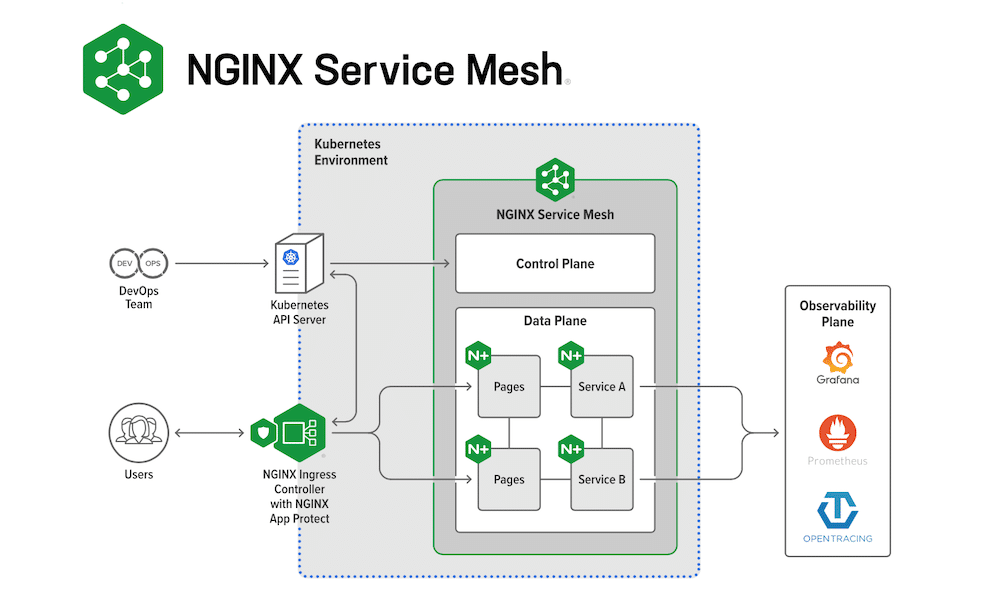
It manages data traffic between containers using the data plane powered by Nginx Plus. Nginx service mesh focuses on the following.
- Security: mTLS‑encrypted traffic between services.
- Traffic management: Policy-managed traffic control between services with rate limiting and circuit breakers.
- Visualization: Inbuilt Grafana dashboard provided visibility into NGINX plus metrics.
- Hybrid deployments: Legacy applications can community with service mesh through the Nginx ingress controller.
8. Kuma
| Github | Kuma Open Source repo |
| Official Website | kuma.io |
| Learning | Kuma Official Documentation |
Kuma service mesh was originally created by Kong, Inc and is now a CNCF sandbox project. It is built on top of the Envoy proxy. It can act as a service mesh for both the kubernetes cluster and VMs.
Following are the key features of Kuma
- Universal Control Plane
- Lightweight Data Plane
- Multi-Mesh
- mTLS & TLS rotation
- Fault Injection
- Traffic tracing and traffic metrics
- Platform-Agnostic
- Transparent proxying
Other Service Mesh Tools To Consider
Following are the other CNCF-based service mesh tools to look at.
- Meshery
- Gloo Mesh
- Grey Matter
- Service Mesh Interface
- Network Service Mesh
Here are some of the cloud-managed service mesh services.
That’s a Wrap.
There you have it – my list of the best service mesh tools.
When making your choice, first dig deep into the service mesh features. You should be able to adapt your organization's needs with the features provided by the Service Mesh tool.
Second, decide if you have the team with the skillsets to implement and manage the tool. Initial setup is always easy, the actual trouble comes in its lifecycle management.
So pick the best option tailored just for your project needs.
I will keep updating this blog with the latest information about the tools and their releases.
Also, if you want to look at a comprehensive list of tools that can be used in the DevOps toolchain, check out the devops tools list where I have covered 90+ best tools in different categories.
If you’re looking for a good container orchestration platform, read my reviews on the best container orchestration platforms.

