In this blog, I discuss concepts, tips, and tricks related to AWS ARN. I will also explain how to create ARN URLs for specific AWS resources.
I have also added all the important links to AWS resources to quickly build the ARN you need.
What is ARN in AWS?
Amazon Resource Name (ARN) are unique identifiers assigned to individual AWS resources. It can be an ec2 instance, EBS Volumes, S3 bucket, load balancers, VPCs, route tables, etc.
An ARN looks like the following for an ec2 instance.
arn:aws:ec2:us-east-1:4575734578134:instance/i-054dsfg34gdsfg38Why are ARN Important?
ARN play a crucial role in IAM policies. You will end up using ARN if you follow the standard security best practices for IAM roles and policies.
ARN have the following key use cases.
- They are used in IAM policies for granting restricted granular access to resources. One example is to allow a specific IAM user to access only specific ec2 instances.
- It can be used in Infrastructure as Code scripts and API calls to refer to other resources. You can see a practical example in the Terraform IAM role creation blog.
If you did not understand the above points, don't worry, we will look at those with practical examples in the following topics.
AWS ARN format
In most cases, you can build the ARN URL yourself following the below format.
arn:aws:service:region:account-id:resource-id
arn:aws:service:region:account-id:resource-type/resource-id
arn:aws:service:region:account-id:resource-type:resource-idIn the above formats, towards the end, you can see the difference in the formats which changes as per the resource types.
Here are the arn examples for all three formats.
S3 ARN Example: S3 has a flat hierarchy of buckets and associated objects. Here is what an S3 ARN would look like
arn:aws:s3:::devopscube-bucketEC2 ARN Example: ec2 service has sub resource-types like image, security groups etc. The following example uses the instance resource-type.
arn:aws:ec2:us-east-1:4575734578134:instance/i-054dsfg34gdsfg38Lambda ARN Example: Lambda functions can have multiple versions. Here the version is the qualifier. To have arn of the specific Lambda version, you need to mention the version number at the last as shown below
arn:aws:lambda:us-east-1:4575734578134:function:api-fucntion:1Components of an ARN
ARN structure consists of several components and the arn structures used in AWS are given below
arn:partition:service:region:account-id:resource-id
arn:partition:service:region:account-id:resource-type/resource-id
arn:partition:service:region:account-id:resource-type:resource-idThe components are listed below in detail
- ARN - Every arn begins with this prefix.
- Partition - This specifies the region in which the AWS account is in, AWS is the partion for most resources.
There are also other particion, aws-us-gov for US government resources and aws-cn for resources in China. - Service - The service specifies the AWS service to which the resource is belong to. For example it will be arn:aws:ec2: for EC2 and arn:aws:s3: for S3.
- Region - This component specifies the region in which the resource is located.
It is only available for regional resources like EC2 and will not be available for global resources like IAM. - Account ID - Specifies the account ID of the AWS account in which the resource is in.
- Resource Type - This component is not available for all resources, it is only available for resources which are inside a service with multiple resources.
For example, EC2 has multiple resources like Instance, AMI, etc,.. Resource Type is used for these resources. - Resource ID - This is a unique identity for resources within the AWS account.
How to get the ARN of AWS resources?
If you are getting started with AWS, you may find it difficult to put together the correct arn URL for a resource.
You can find the syntax for ARN for all the AWS services here.
For example, in that AWS document, if you go ec2 resource from the list, and scroll down to the "Resource Types Defined by Amazon EC2" section, you will find the reference for all the sub rsource types for ec2 as shown below.
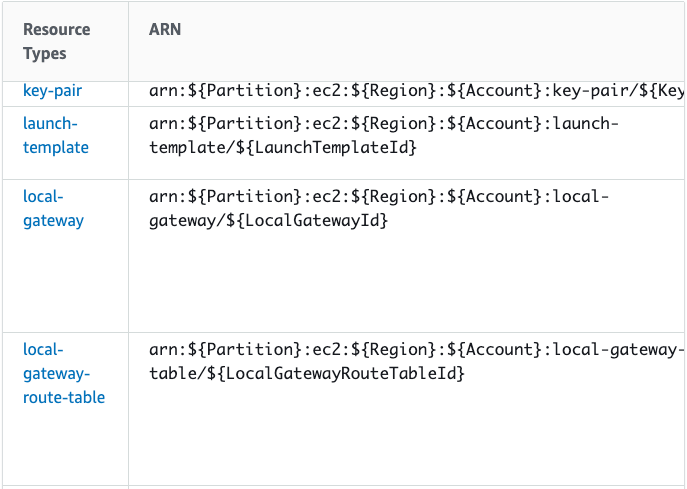
Another way is to use the aws policy generator.
In the policy generator, when you select the policy resource, it will automatically show the arn suggestion as shown below. You just need to add resource information.
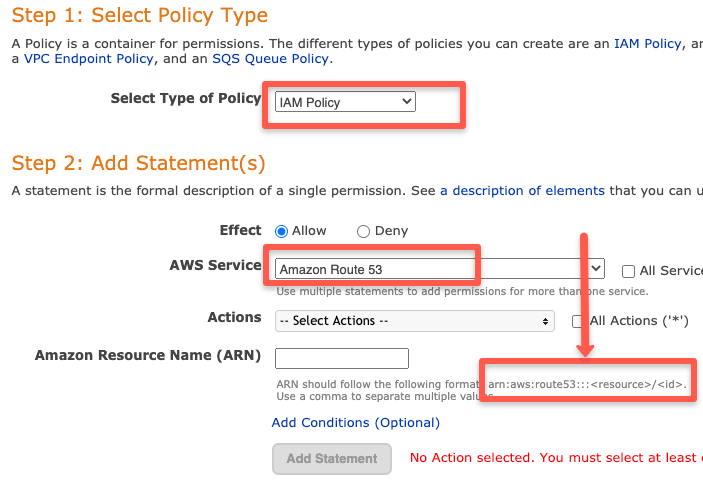
ARN Wildcards
ARN definition supports wildcards. You will need a wildcard in many use cases.
Let's say you want an IAM policy that allows access to all objects in a single bucket. For this, you can have a wildcard arn like below.
arn:aws:s3:::my-data-bucket/*Here is an example of using wildcard arn in an IAM policy. This policy allows all actions for dcubebucket S3 bucket.
{
"Version": "2012-10-17",
"Statement": [{
"Sid": "Stmt1596173683332",
"Action": "s3:*",
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::dcubebucket",
"arn:aws:s3:::dcubebucket/*"
]
}]
}Here is another example policy that allows limited access to all emr clusters.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1596174145144",
"Action": [
"elasticmapreduce:AddInstanceFleet",
"elasticmapreduce:AddTags",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:DescribeEditor",
"elasticmapreduce:DescribeJobFlows",
"elasticmapreduce:DescribeSecurityConfiguration"
],
"Effect": "Allow",
"Resource": "arn:aws:elasticmapreduce:*:*:cluster/*"
}
]
}ARN Paths
In some cases using wildecard is not recommend monstly in IAM policies which can give access to evey resiurces comes under the wildcard, this is where path comes in handy.
Paths are used to identify specific resources inside a resource type and it is a way to structure resources within AWS services that support hierarchical resource naming.
Paths are specified at the end of the arn, and each path is separated by ( / ) based on its path structure.
For example, if you want to give access to a group of users to a specific folder inside the bucket while restricting access to all other folders on a bucket, you can use arn paths to give access only to a specific folder
arn:aws:s3:::example-bucket/folderHere is an example of using arn path in an IAM policy. This policy allows the user to access only the folder dev inside the dcubebucket S3 bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::dcubebucket/dev/*",
"Condition": {
"StringLike": {
"aws:userid": "12345678910/development/*"
}
}
}
]
}
This policy gives access to users who come under development on the folder dev inside the S3 bucket dcubebucket.
Getting ARN from AWS CLI
You can get the ARN of specific resources from the CLI.
For all IAM roles, policies, and users, you can get the ARN from the CLI by describing it.
Here is an example of getting arn of a role.
aws iam get-role --role-name EMR_DefaultRoleHere is the output with the arn.
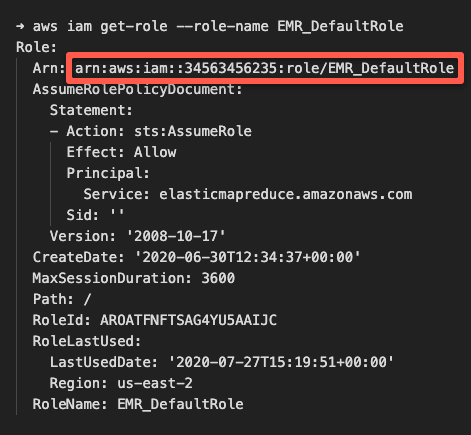
Like this, you can try describing the resource and see if it outputs the arn.
Getting ARN from AWS Console
You can get the arn of IAM resources directly from the AWS console.
Just browse to the specific resource and you will find the related arn at the top as shown below.
Getting ARN as Output in Cloudformation
If you are using Cloudformation, you can get the resource arn in the output with the function Fn::GetAtt
Here is an example syntax of getting the arn of a Lambda function.
resources:
Outputs:
LamdaFunctionArn:
Export:
Name: MyFucntionARN
Value:
Fn::GetAtt: MyLambdaFunction.ArnGetting ARN of Principal
When you create an S3 bucket policy, SNS topic, VPC endpoint, and SQS policy, you need to specify a principal parameter.
Principal Is the trusted source specified as an ARN in the policy to allow or deny access to the resource
For example, if you want an S3 bucket to be accessed only by a specific user, you will specify the user arn as Principal in the policy.
If you use a Policy generator to create these policies, you will see the principal option as shown below.
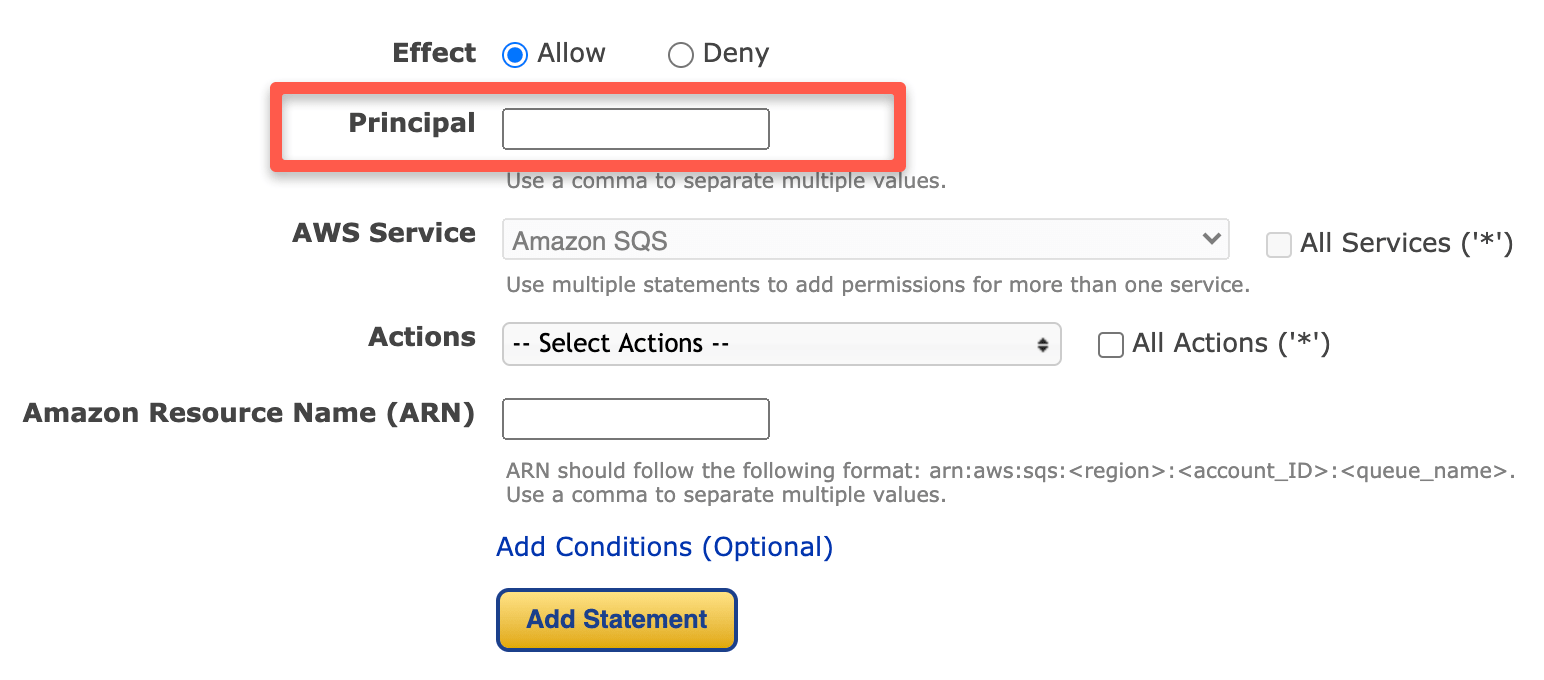
Primarily you specify the user, account, and role arn as the principal. There are other Principal sources as well. Please see this AWS document to learn more.
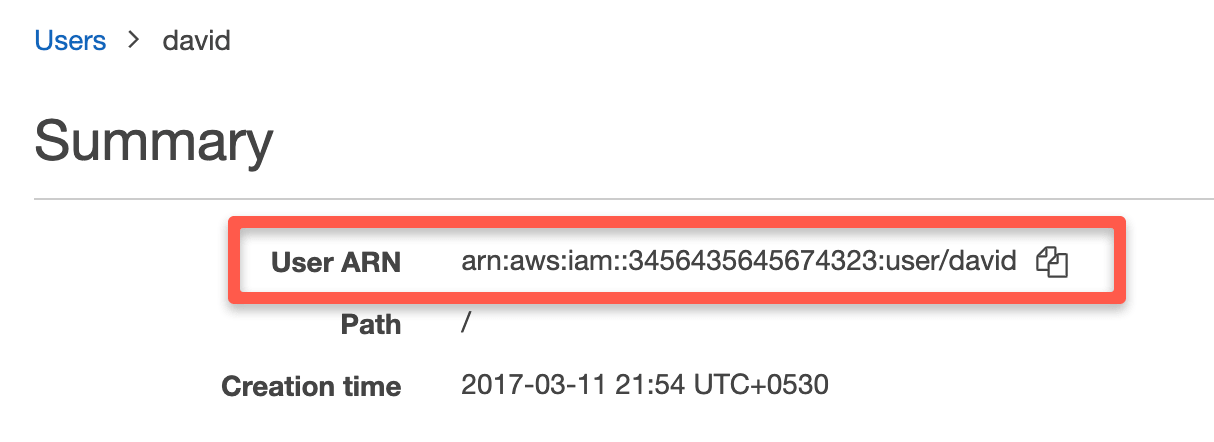
Getting the User arn
If you browse the user page in the AWS console, you will get the user arn as shown below.
AWS Account arn
AWS account arn has the following syntax. Replace account-id with your account id.
arn:aws:iam::<account-id>:rootGetting an AWS Role arn
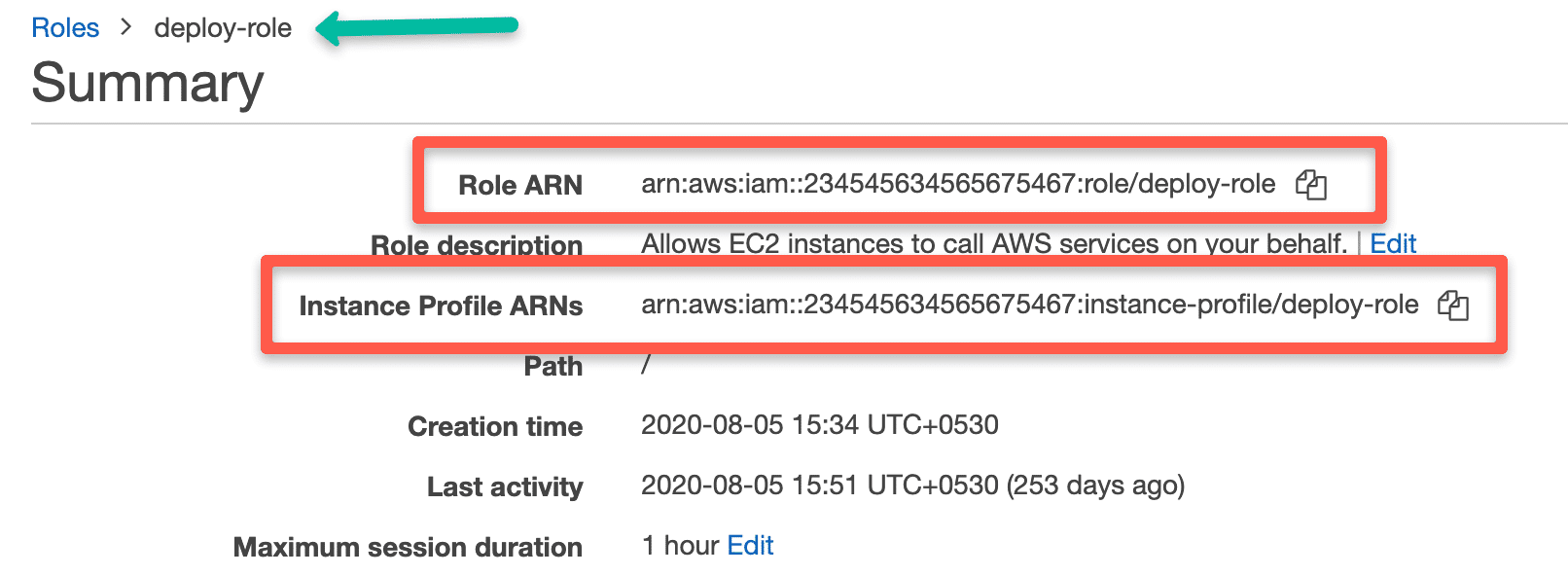
You can get the arn of the IAM role from the cli as explained in the above section.
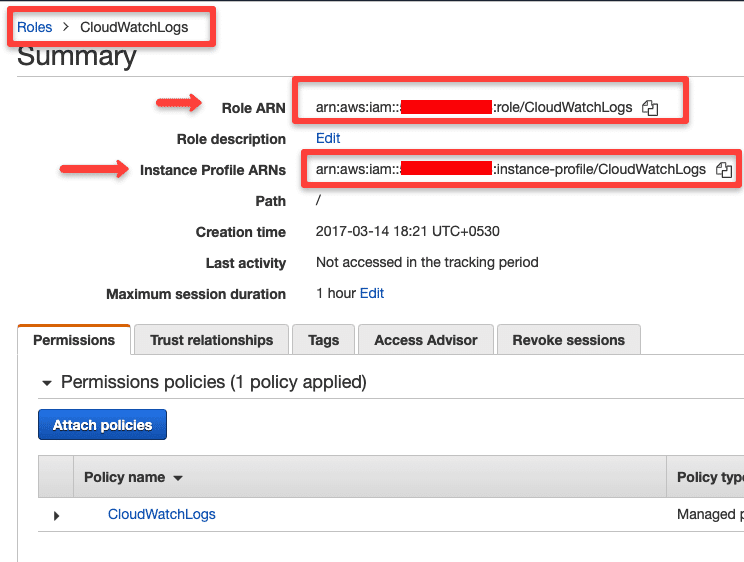
If you go to IAM --> Role --> Your role from the web console, you can view the arn as shown below.
Wrapping Up
I have added some of the resources and tricks I use for aws arn.
I would like to hear from you.
Please let me some scenarios you have come across in the comments section.
You might also like AWS Load Balancer Concepts.

