Probably you would have heard of security incidents that involve secrets being uploaded to public code repositories by accident.
So before getting into the details for Deadshot, I would like to go through some of the security incidents that happened through Github
- AS per news in Gizmodo, An amazon DevOps Engineer committed nearly a gigabyte of data to a personal Github repository that included token, API keys, passwords, and cryptographic keys to various AWS environments
- 2019 ZDNet article says Over 100,000 GitHub repositories have leaked API or cryptographic keys. This was academic research carried out by a team from the North Carolina State University (NCSU)
- In 18 months, a Netherlands-based security researcher found and reported GitHub credential exposure problems directly to more than 400 organizations, including cybersecurity firm Comodo.
Probably by now you realize how serieous is this problem
Anyhow, developers pushing secrets to public repositories is not something you can control because it is the individual responsibility to keep the organization's data safe in their systems.
However, there is a way to stop developers from committing secrets to GitHub repos owned by the organizations.
Here is where DeadShot comes in to picture.
About Deadshot From Twilio
Deadshot is developed by Twilio
So what is Deadshot all about?
Here is what the repo says about Deadshot. (https://github.com/twilio-labs/deadshot)
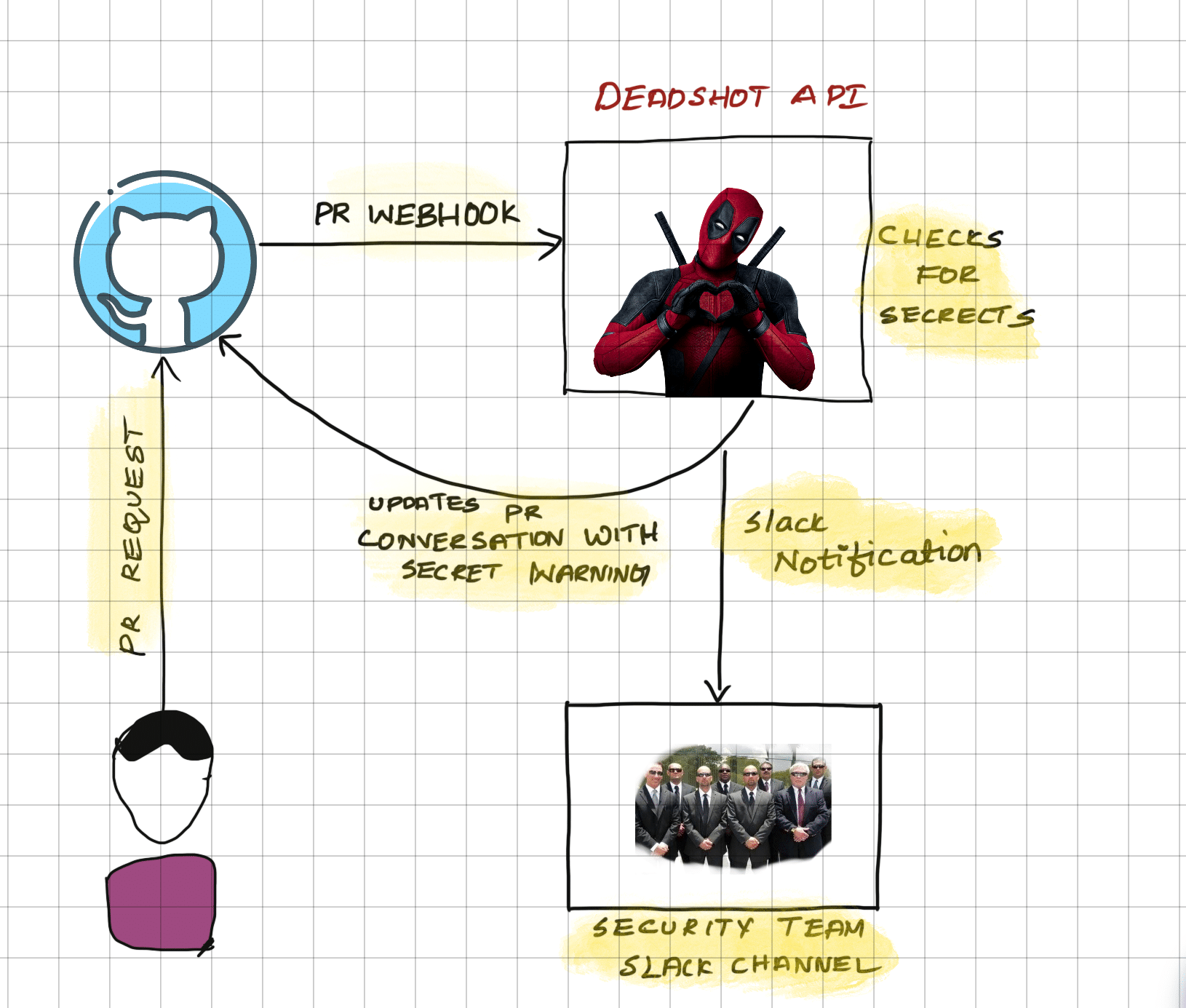
Deadshot is a Pull Request scanner that looks for the introduction of secrets via pull requests by matching each diff line against a set of known secret expressions.
Menning, DeadShot processes the PRs in real-time to check if there any secret being committed.
When it finds a secret, it notifies the user in the PR conversion.
or, it can send slack notifications to security teams channel.
Deadshot is built using Python Flask, Celery, and Redis. It should be deployed in an environment and the API endpoint would be configured as an APP in Github to read and process all the Pull requests.
Many organisations still use Github for storing API tokens and other secrets which is really really bad.
You repos may be private and secure. However, there is chance where developers local copy getting pushed to public repositories.
Consider using solutions like Hashicorp Vault to store and retrive secrets.
Also, all the major cloud providers have managed secret management solutions that integrated well with all the services.

