SSH (Secure Shell) Key is the secure way to log in to Linux servers as compared to passwords.
Every DevOps engineer has to use SSH key-based authentication when working with Linux servers. Also, most cloud platforms offer and recommend SSH key-based server authentication for enhanced security
This blog post aims to provide a detailed, step-by-step guide on how to create an SSH key pair for authenticating Linux servers and applications that support SSH protocol using SSH-keygen.
SSH-Keygen
ssh-keygen is the utility to create SSH keys. It is part of every Linux and MAC system.
You can use the man command below to understand the ssh-keygen utility and all available options.
man ssh-keygenOr you can refer to the ssh-keygen online man page
Let's look at different ways and options to generate SSH keys.
Steps to Create an SSH Key
Follow the steps given below to create an SSH key.
Step 1: Open the Terminal
Open the workstation terminal if you are using a laptop to Desktop.
If you are using a headless server, proceed to the next step.
Step 2: Generate the Key Pair
Execute the following ssh-keygen command to generate the SSH key pair. It generates and saves the Keys in the default $HOME/.ssh location. By default, the private key is named as id_rsa , and the public key is named as id_rsa.pub
ssh-keygenStep 3: Save the Key
The ssh-keygen command will prompt for the following options.
- Enter the file in which to save the key:- Local path of the SSH private key to be saved. If you don't specify any location, it gets stored in the default SSH location. ie,
$HOME/.ssh - Enter passphrase: A passphrase is used to protect the SSH private key. You can leave this empty. If you choose to add a passphrase, you will have to enter it again.
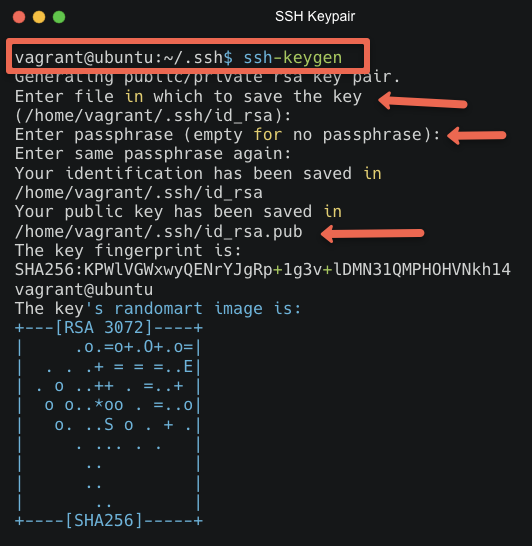
Step 3: Key Created
You've successfully created an SSH key pair. You'll find two files: id_rsa (private key) and id_rsa.pub (public key), usually in the ~/.ssh/ directory.
Generate SSH Keys With Custom Options
Let's take a look at an example ssh-keygen command to generate SSH keys with custom options.
The following command generates an SSH key named ssh-key in the $HOME/.ssh location with username vagrant with -C flag and passphrase mysecret with -q -P flag.
ssh-keygen -t rsa -f ~/.ssh/ssh-key -C vagrant -b 4096 -q -P "mysecret"Let's understand the flags.
- -t rsa: It is the ssh key algorithm. It is the default algorithm used by
ssh-keygen. - -f : keyfile name.
- -q -P: To add passphrase without prompt
- -b: Key Encryption Level. The default is 2048 bits
- -C: To set the comment in the last line of the public key. It is typically used to replace the default username set by the command. You can also use this flag to set the server username.
If you add the Linux username to the key file with -C , you can directly perform SSH without specifying the username in the SSH command.
For example,
ssh -i ~/.ssh/ssh-key 192.81.209.247If you don't want a passphrase and create the keys without a passphrase prompt, you can use the flag -q -N as shown below.
ssh-keygen -t rsa -f ~/.ssh/ssh-key -C vagrant -b 2048 -q -N ""How to Use Your SSH Key
Now that you have created the SSH key, you can use it as a server for SSH authentication.
Here is how you can do it.
Use ssh-copy-id command or manually place the id_rsa.pub file content into the ~/.ssh/authorized_keys file on the remote server.
Use the ssh command as given below
ssh username@remote_serverIf you have saved the SSH key with a different name other than id_rsa to save it to a different location, use the following format.
ssh -i /path/to/private-key-file username@remote_serverFor example,
ssh -i ~/.ssh/ec2-server.pem ubuntu@34.56.76.34Supported SSH key algorithms
SSH (Secure Shell) supports multiple key algorithms for better security. The following are the supported SSH key algorithms.
- Rivest-Shamir-Adleman (RSA): Generally considered secure with key lengths of at least 2048 bits.
- Digital Signature Algorithm (DSA): Limited to 1024-bit key length, making it less secure.
- Elliptic Curve Digital Signature Algorithm (ecdsa): Provides high security with shorter key lengths (256-bit and above).
- Ed25519 - EdDSA signature scheme using SHA-512 (SHA-2) and Curve25519. It offers High security with a 256-bit key length.
Choosing the algorithm depends on your security requirements. One real-world example is the Amazon ec2 ssh key pair. It supports ED25519 and 2048-bit SSH-2 RSA keys for Linux instances.
To check the algorithm of an existing key you can use the following command.
ssh-keygen -l -f ~/.ssh/id_rsaSSH Key FAQs
How do I manually generate SSH keys?
You can manually generate the SSH key using the ssh-keygen command. It creates the public and private in the $HOME/.ssh location.
Is it possible to use ssh-keygen to create an SSH key without a passphrase?
Yes. If you leave the passphrase prompt empty, the ssh keys get generated without any password. You can also pass the flag -q -N "" to the ssh-keygen command to avoid the prompt.
What if I lose my SSH key?
If you lose your private key, remove its corresponding public key from your server's authorized_keys file and create a new key pair. It is recommended to save the SSH keys in a secret management tool.
Can I use the same SSH key for multiple servers?
Yes, you can use the same public key on multiple servers. You just need to add it to each server's authorized_keys file under ~/.ssh directory.
How to create an SSH key online?
It is advisable not to use any online services to create SSH keys. As a standard security best practice, use the ssh-keygen command to create the SSH key.
Conclusion
In this guide, we looked at important commands to create SSH public/private key pairs. It adds a critical layer of security to your Linux systems.
When it comes to SSH keys, always follow the security best practices to avoid private key misuse.
If you are learning Linux, check out the Best Linux Networking and Troubleshooting Commands.
Also, If you are starting your journey as a DevOps Engineer, check out my DevOps Engineer Roadmap.
Note: Always follow best security practices when dealing with SSH keys to ensure your systems remain secure.

