In this blog, we will learn about AWS tag policies, their importance, use cases, and syntax. We will also look at best practices to use them in an AWS account.
AWS Organizations
AWS Organizations is an account management service that helps to manage multiple AWS accounts centrally.
Typically every organization would have different organization units (OU) and every OU may have different teams and every team has its own AWS accounts (member accounts).
AWS Organization is capable of creating Organizational Units (OUs). These organizational units will maintain the member accounts.
The following image shows root, OUs, and member accounts.
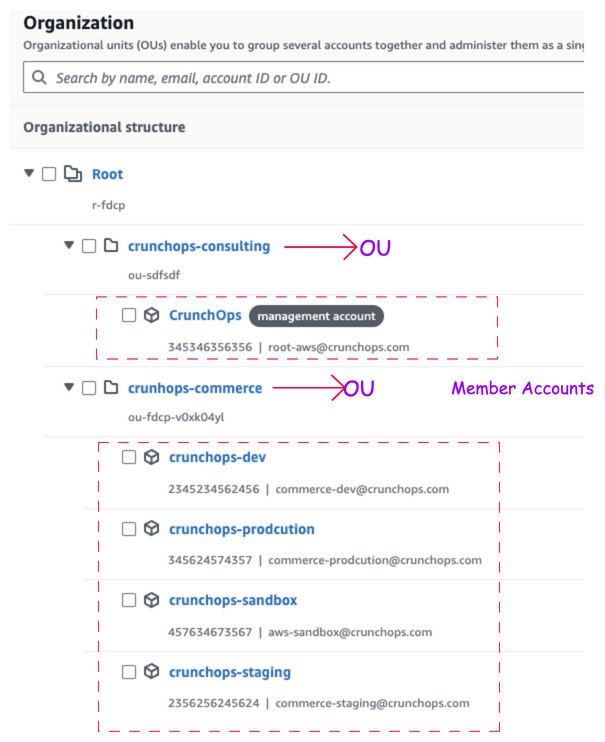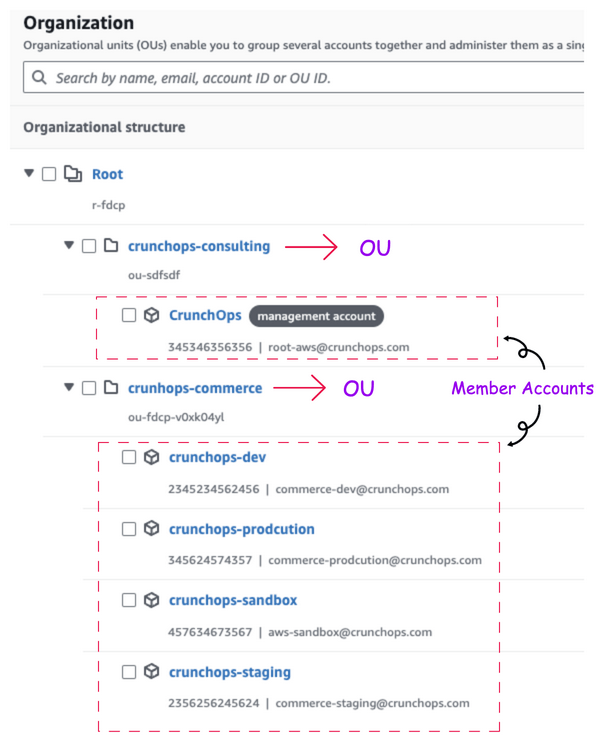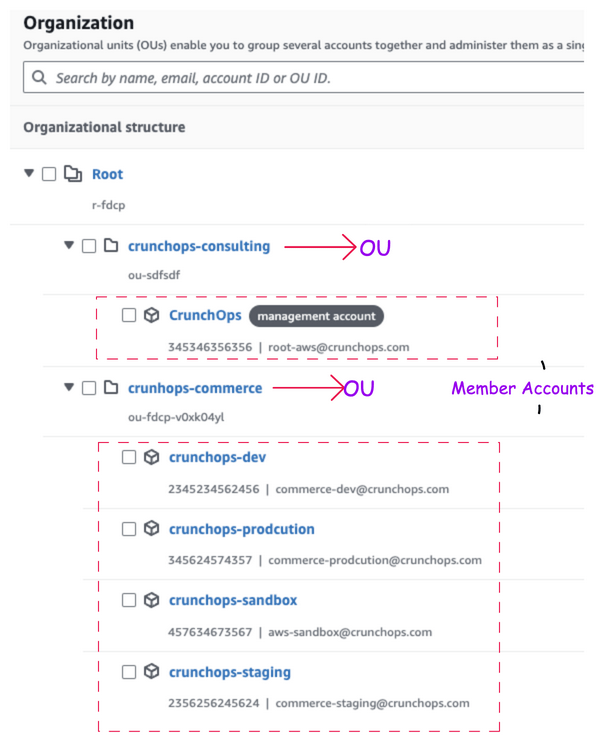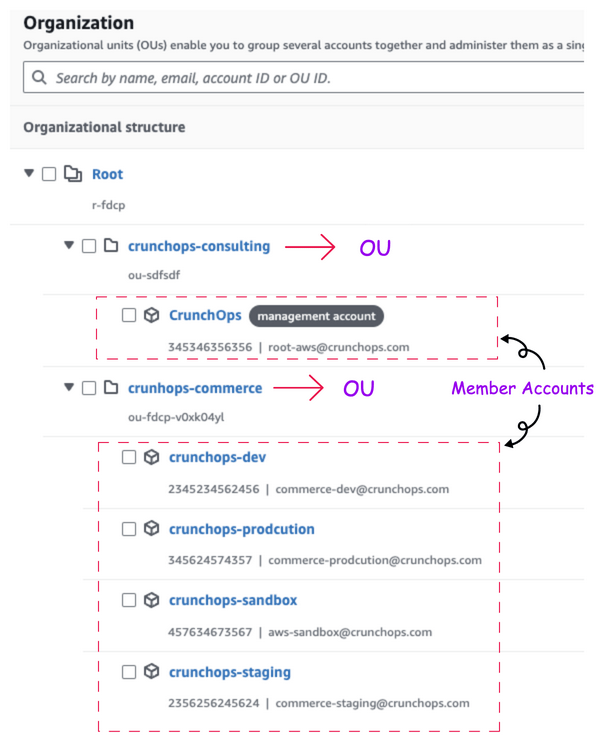
AWS Tags
AWS tags are small pieces of metadata that can be attached to various AWS resources, such as Elastic Compute Cloud (EC2) instances, Simple Storage Service (S3) buckets, and Relational Database Service (RDS) instances.
A tag has two parts, one is tag key and the other one is optional which is tag value.
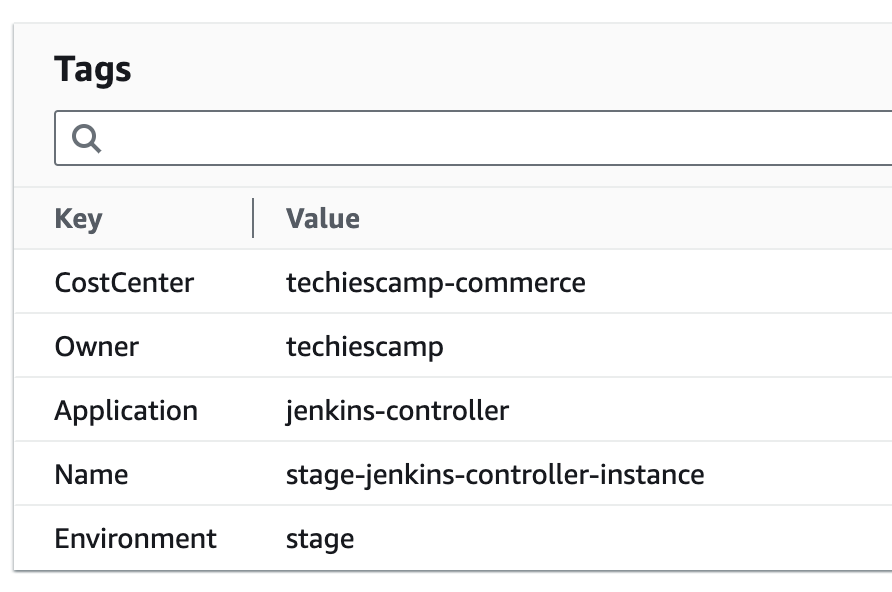
Here is an example of tags attached to an ec2 instance.
Resource Tagging and its Importance
Let's look at why resource tagging is important in AWS.
- Organize Resources: Organize AWS resources with certain categories. For example, if there are different environments, allocating tags separately allows users to easily identify their resources in a large organization.
- Cost Tracking: Track the costs category-wise with the related tags. It is one of the very important practices to track costs in cloud computing, and it also helps to create budget plans.
- Security Compliance: Through tags, policies can be attached to restrict the provisioning of certain resources. For example, enforcing tag value compliance for a particular resource ensures that without the proper key, no one can provision that resource.
Here are some best practices to follow,
- Tagging Policies: To prevent untagged resource provisioning, attach a tag policy that enforces compliance with tagging requirements.
- Minimal Tags: Avoid creating excessive tags; instead keep them short and meaningful. This approach helps to easily understand their usage and avoids unnecessary confusion.
- Tag Review: Periodically review the tags. and update them as per the changes in requirements. This practice will improve the accuracy of tracking resources.
What is AWS Tag Policy?
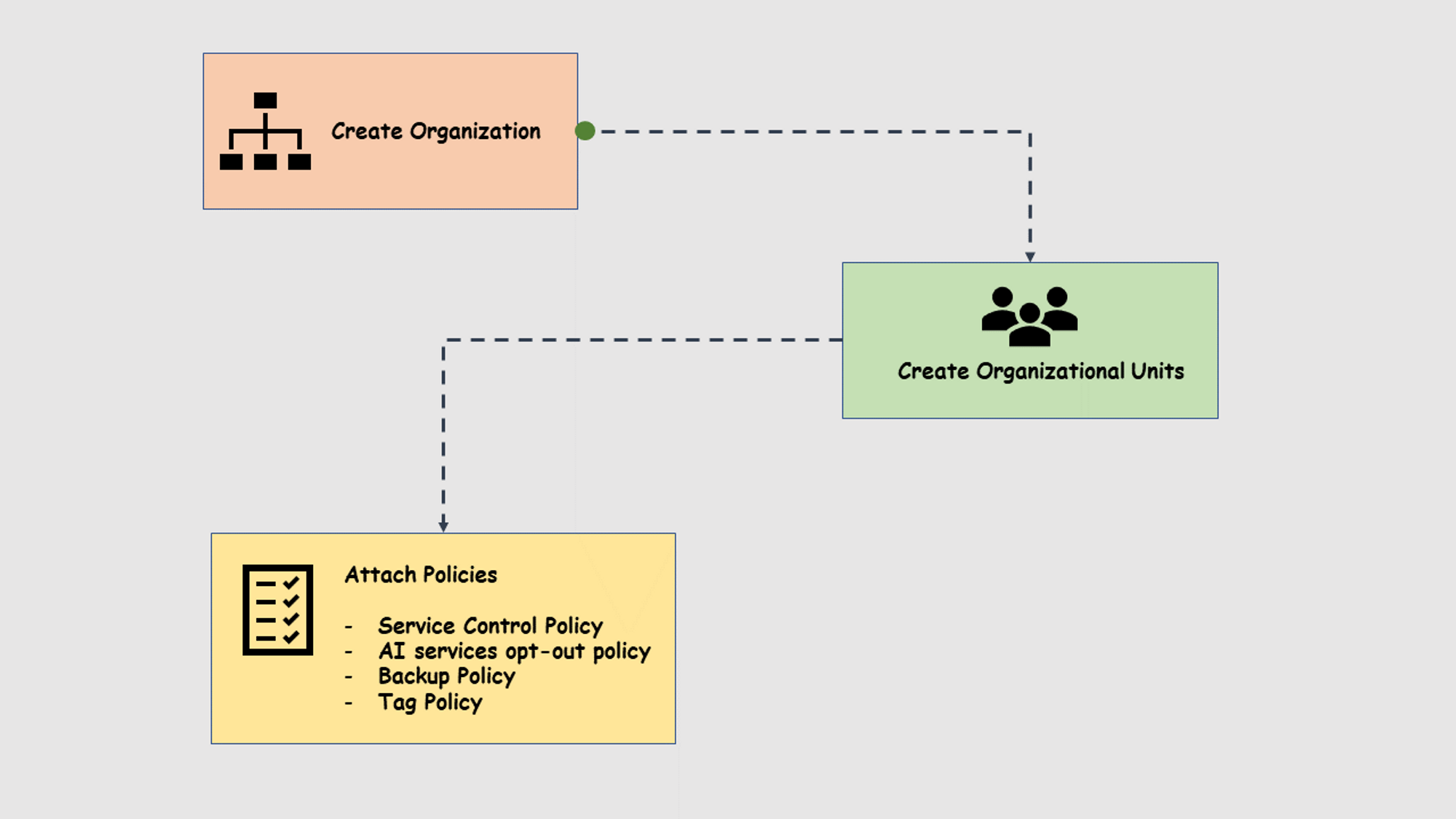
AWS Organizations Tag Policy is used to standardize AWS resource tagging. The Tag Policy applies certain rules to resources when they are created.
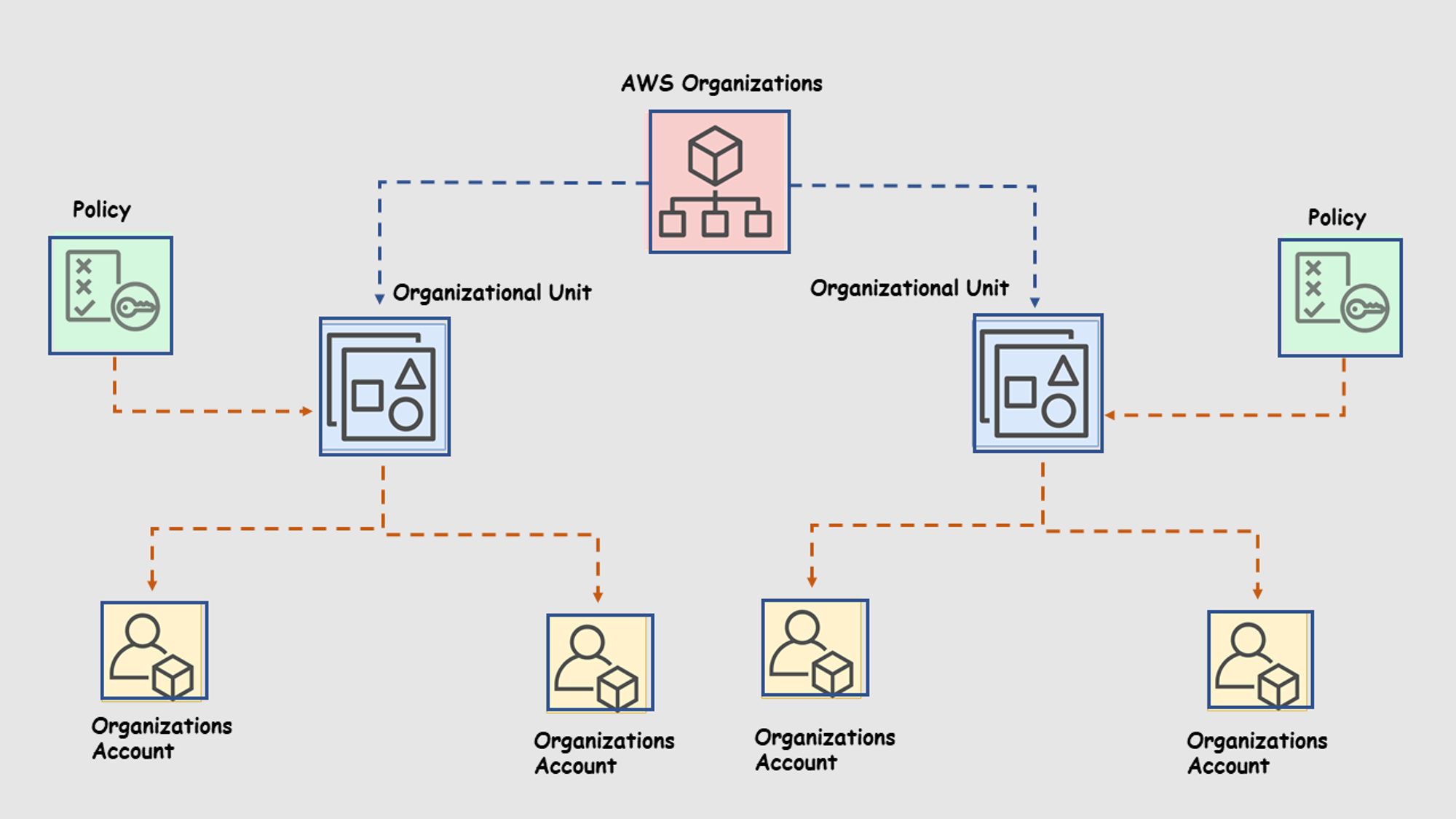
All policies applied to organizational units are applied to all organizational accounts.
Tag Policy Syntax
The tag policy is structured in a simple JSON format. so it is easy to create and manage rules.
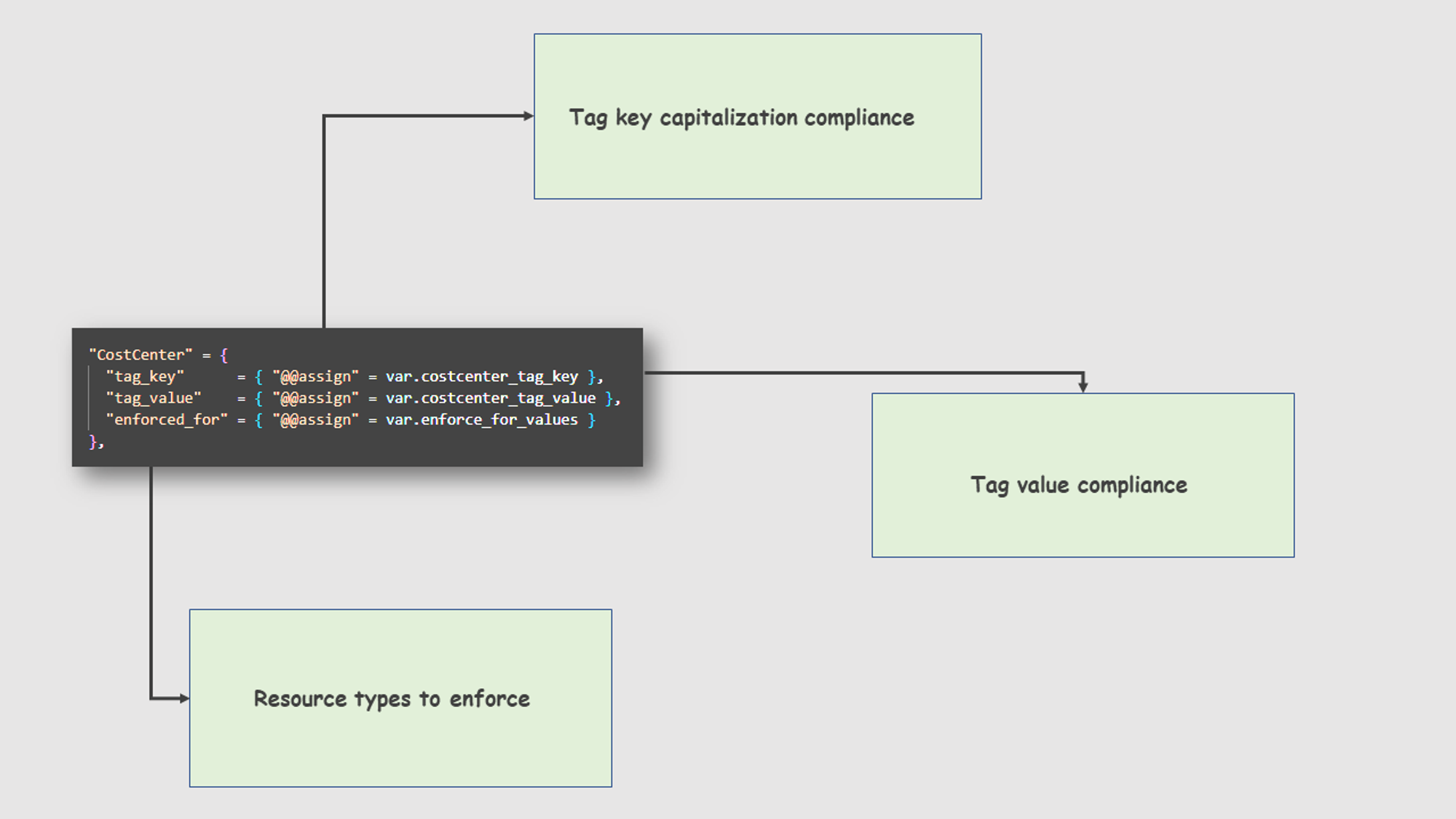
Tag key capitalization compliance
Tag keys are case-sensitive. If tag key compliance is not enabled, it will automatically take the tag key as lowercase. Alternatively, if any kind of capitalization compliance is specified in the parent policy, it will be applied to the other policies as well.
So, to avoid these confusions, enable tag key capitalization compliance. This means that wherever the tag key is mentioned, the exact same name has to be given. For example, here the tag key name is CostCenter , and if try to launch a resource with the tag key COSTCENTER or costcenter , it will show an error message.
Tag value compliance
Tag values are subject to specific rules set for tag keys. They represent the actual value that can be seen after the resource has been created. often serving as the resource name. If not enable tag value compliance, can give any value for the tag key.
However, in this case, enabled tag value compliance for the CostCenter tag key with the value techiescamp-commerce. Therefore, when using the CostCenter tag key, only the techiescamp-commerce tag value can be used; Otherwise, the resource won’t be created.
Note: You can also use AWS Config service for Tag complinace. The only difference is, AWS config helps you remediate the tag compliance. You cannot enforce rules using config service. However, you can monitors existing tags and checks if they comply with the rules you set.
Resource types to enforce
Specify certain resource types for this tagging strategy so that the rules only apply to those resources. By enabling the Prevent non-compliant operation feature, ensure that for those particular resources, a specific tag key and tag value must be provided during launch.
In this case, multiple resource types are mentioned, for example: ec2:instance, ec2:security-group, elasticfilesystem:*, lambda:*, etc.Therefore, when launching a resource, the proper tag key and tag value must be provided.
Note: Forenforce_for, for some services, can useall resources. For example, to enable tag policy in all resources for AWS Backup, can usebackup:*. However, it is not possible to enable tag policy for all resources in Amazon EC2. To know more about the supported services, visit the official documentation.
Automating Tag Policies Using Terraform
It is always better to manage the tag policies as part of the IaC.
I have created a step-by-step terraform guide to configure tag policies for an AWS account.
Checkout AWS Tag Policy Configuration Using Terraform
Conclusion
As Devops Engineers, it is very important to maintain AWS resources with recommended tags from the organization.
With tag policies, you can enforce organization-wide tags for all the supported AWS resources. This ensures no resources get deployed without required tags.
Furthermore, with tools like Checkov, we can implement tag checks before the IaC code gets committed to the main branch.
Also, check AWS security tips if you are getting started with AWS.


